Identifying Security Gaps in International Postal and Transportation Infrastructure
PUBLISHED IN
Enterprise Risk and Resilience ManagementIn October 2010, two packages from Yemen containing explosives were discovered on U.S.-bound cargo planes of two of the largest worldwide shipping companies, UPS and FedEx, according to reports by CNN and the Wall Street Journal. The discovery highlighted a long-standing problem--securing international cargo--and ushered in a new area of concern for such entities as the United States Postal Inspection Service (USPIS) and the Universal Postal Union (UPU), a specialized agency of the United Nations that regulates the postal services of 192 member countries. In early 2012, the UPU and several stakeholder organizations developed two standards to improve security in the transport of international mail and to improve the security of critical postal facilities. As with any new set of standards, however, a mechanism was needed to enable implementation of the standards and measure compliance to them. This blog post describes the method developed by researchers in the CERT Division at Carnegie Mellon University's Software Engineering Institute, in conjunction with the USPIS, to identify gaps in the security of international mail processing centers and similar shipping and transportation processing facilities.
Foundations of Our Approach
This engagement was not our first time working with the USPIS. Our first project, in 2011, involved helping USPIS ensure that packages sent to other countries from the United States complied with U.S. export laws. As a result of this initial engagement, USPIS had a well-defined process for addressing export law compliance. In addition to export screening, we have worked with USPIS on projects that involve incident response, authentication services, physical security, aviation screening for international mail, Priority Mail Express revenue assurance, and the development of mail-specific resilience management process areas for mail induction, transportation, and revenue assurance.
The projects that we've worked on with the USPIS draw upon the CERT Resilience Management Model (CERT-RMM). CERT-RMM is a capability-focused maturity model that combines aspects of IT operations management with operational risk and resilience management, such as information security and business continuity.
In response to the discovery of explosives in the two packages from Yemen and the subsequent development of new security standards by the UPU, the USPIS asked our team, which included David White, Pamela Curtis, and Julia Allen, to use the CERT-RMM assessment method and process to develop an assessment methodology along with a companion field instrument for the following two UPU standards:
- S58, Postal Security Standards--General Security Measures defines the minimum physical and process security requirements available to critical facilities within the postal network.
- S59, Postal Security Standards--Office of Exchange and International Airmail Security defines minimum requirements for security operations relating to the air transport of international mail.
Based on the requirements and design criteria that USPIS had specified, our team was faced with the development of a methodology and an associated field instrument that had to be repeatable (i.e., generate consistent results when used by different teams in the same situation); cost effective and scalable (i.e, economical and functional for all locations); accurate (i.e., evidence-based); meaningful (i.e., results could easily be acted on by owners and operators of the assessed facilities); and transparent (i.e., publicly available and could be used for self-assessment).
One challenge in developing an assessment methodology based on UPU standards was contending with the ever increasing interweaving of physical and cyber domains. Securing even a mundane physical asset, such as a parcel, involves controlling both tangible and intangible objects, such as computer systems, networks, processes, and sensors.
Another challenging aspect of this work was that the UPU standards were not developed with much consideration as to how member countries would use them to assess whether mail processing facilities were in compliance. This challenge made it hard to develop the streamlined approach that USPIS was seeking to evaluate mail processing facilities that handle international mail.
A Proven Method
As depicted in the figure below, our team developed a methodology that defined three phases for conducting the assessment:
- Preparation: Analyze requirements, develop an assessment plan, select and prepare the assessment team, send and receive the pre-assessment questionnaire, obtain and inventory objective evidence, and prepare for the conduct of the assessment (initial site visit and logistics).
- Onsite: Prepare participants, conduct interviews, examine objective evidence, document objective evidence, verify objective evidence, perform characterizations and ratings, formulate and validate preliminary findings, generate the final results of the assessment, and identify improvements to the method and the standards.
- Reporting: Deliver assessment results to sponsors and key stakeholders, and preserve and archive assessment results.
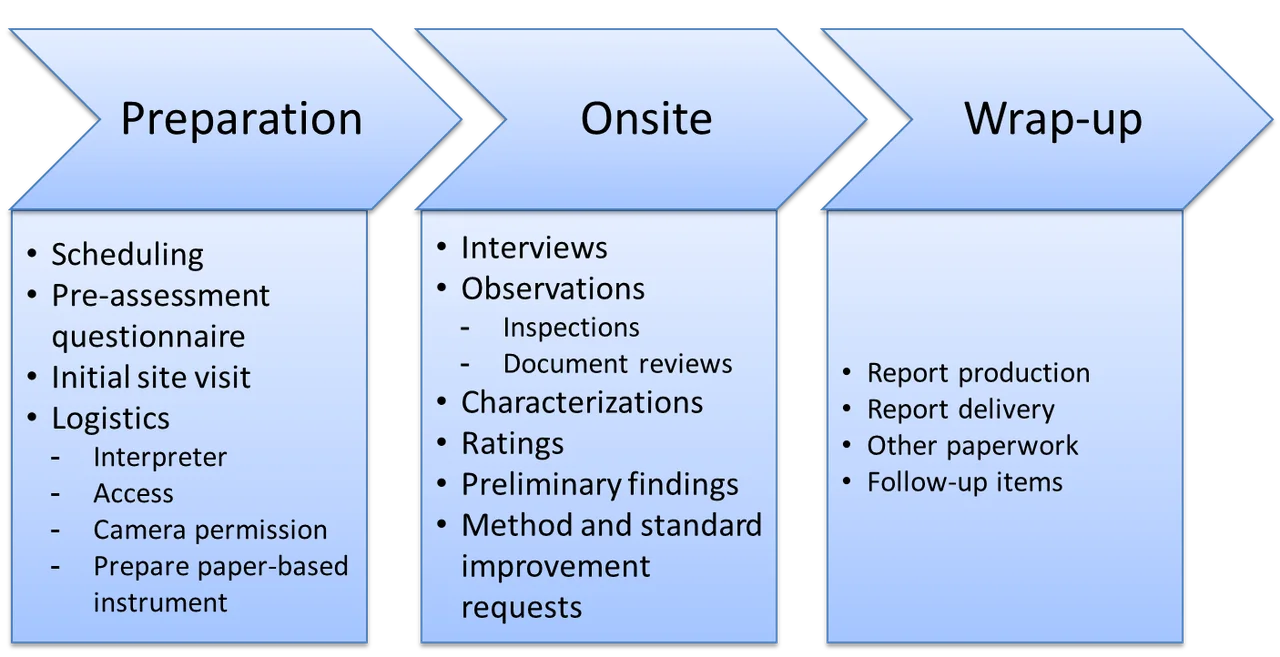
The questionnaire-based assessment instrument developed by our team contains a series of questions. Below are some examples of the types of questions included, as well as the areas (in bold type) that they cover:
- Risk Management: Do you conduct an annual risk assessment of each critical facility?
- Physical Security: Do you have a written facility security plan?
- Physical Security: Are facilities constructed to prevent illegal entry?
- Access Control: What is the process for the control, issuance, and removal of identification badges?
- Human Resources: Do you have a documented personnel selection and hiring policy and process?
- Mail Security: How are high risk mail items identified in the mail stream?
- Transportation: Are routes, schedules, and planned stops assessed for security?
Our methodology also defines the requirements for evidence collection for each section of the standards. The team conducting the assessment must examine documented artifacts or receive oral and written statements and affirmations confirming or supporting the implementation (or lack of implementation) of a practice. If the assessment team observes specific weaknesses in implementation, team members record them on their assessment worksheets. For example, a weakness in implementation of S58 Section 5.1.1, Risk Assessment and Facility Security Plans, might be that the facility's security plan covers general lighting requirements, but not interior emergency lighting.
Our field instrument is used by the assessment team to keep track of results of interviews and other objective evidence collected. The assessment team uses this information to rate the degree by which each requirement in the standards is implemented. The assessment team also uses our field instrument to generate a summary of the results, in the form of a colored heat map, which is presented to the facility owners and operators. A small segment of a sample heat map is shown in the figure below. The heat map was designed to be easily understood by all relevant stakeholders, ranging from security operations staff to senior decision makers.
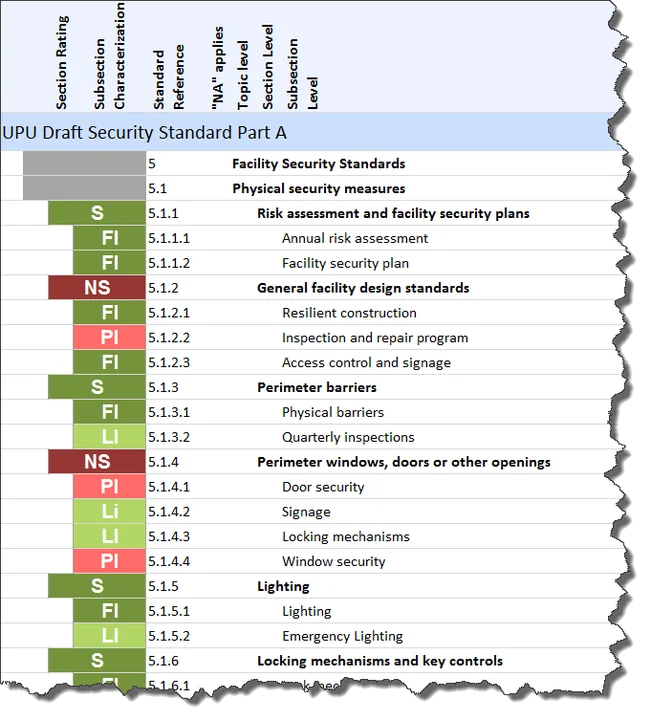
(LEGEND: FI = Fully Implemented; LI = Largely Implemented; PI = Partially Implemented; NI = Not Implemented; S = Satisfied; NS = Not Satisfied.)
Through our research, we aim to transition our solutions to our stakeholders by enabling them to conduct assessments independently. In early 2012, the assessment method was piloted by USPIS staff at several international postal administrations. As a result of one of the USPIS pilot assessments, one of the national postal administrations closed an international mail dispatch facility and moved operations to a new facility with improved security controls and conformance with UPU standards. Other assessments have shown that postal administrations largely conform to UPU standards and that having the specific feedback of assessment results encourages them to make the minor improvements needed to ensure full compliance.
One consistent finding of our pilot highlighted the effectiveness of the method for producing accurate assessments. The S58 standard requires a single, written security plan for critical facilities. While each pilot location that the USPIS assessed maintained a security plan, the plans at those sites did not contain all of the elements that the standard requires, including general facility design standards, perimeter barriers, perimeter windows, doors or other openings, lighting, and locking mechanisms and key controls. The methodology that we developed for the USPIS included evidence-discovery procedures such as direct artifacts, indirect artifacts, and affirmations. These evidence-discovery procedures helped the assessment team locate those elements in other documents such as maintenance plans.
Other benefits that participating facilities cited in field reports and assessment results included:
- insight into the strengths and weaknesses of current security practices
- recognition of a strong security posture by the International Civil Aviation Organization, World Customs Organization, and supply chain partners that rely on postal services for moving goods
- guidance to prioritize security-related improvement plans
- feedback on the maturity of the organization's security program
- enhanced identification and prioritization of security risks
The method, the results, and the overall explanation of the project are detailed in a technical note titled A Proven Method for Identifying Security Gaps in International Postal and Transportation Critical Infrastructure, which I co-authored with Julia H. Allen and Pamela D. Curtis of the SEI and Gregory Crabb of the USPIS.
Looking Ahead
Our work with the USPIS has demonstrated that, when properly interpreted, CERT-RMM can be applied to a wide range of business objectives. For example, CERT-RMM allows for the addition of new asset types (such as mail items) and the development of new process areas (PAs) (such as mail induction and mail revenue assurance), which can be used in concert with existing CERT-RMM process areas. These new PAs reference established CERT-RMM PAs for specific types of processing including the following:
- identification of discrepancies in mail-specific PAs invoke the Incident Management and Control PA, the purpose of which is to identify and analyze events, detect incidents, and determine an appropriate response.
- identification of risks in mail-specific PAs invoke the Risk PA, the purpose of which is to identify, analyze, and mitigate risks to organizational assets that could adversely affect the operation and delivery of services.
In January 2014, we presented our work jointly with the USPIS at the 93rd Annual Meeting of the Transportation Research Board Conference. One message we delivered during that presentation was that moving mail--from the time it is accepted to the time it is delivered--is fundamentally a transportation activity, where the entities being transported are mail items. The security and resilience management techniques we developed for postal administrations are thus also applicable to other transportation modes, as well as to other safety and security standards. These transportation modes include those modes that move people, (such as metropolitan area transit systems) and the transport of goods by air, ground, and sea.
Pilot organizations have shown that using our method, which is ultimately a structured and scripted assessment instrument, is an effective way to assess compliance with the UPU postal security standards. During the 25th Universal Postal Congress in Doha, Qatar, in September 2012, our method was recognized as the approach for assessing compliance with the new UPU security standards. The USPIS and other postal sector organizations continue to use the assessment method to achieve initial results and assess progress made after implementing improvements. In 2014, the method will be provided to civil aviation authorities, who will use it primarily to assess the performance of postal administrations in meeting the screening and other international airmail security standards of S59.
Additional Resources
To read the SEI technical report, A Proven Method for Identifying Security Gaps in International Postal and Transportation Critical Infrastructure, please visit
https://resources.sei.cmu.edu/library/asset-view.cfm?assetid=77265.
For more information about the CERT Resilience Management Model (CERT-RMM), please visit
https://resources.sei.cmu.edu/library/asset-view.cfm?assetID=508084.
To hear Gregory Crabb, Inspector in Charge of Revenue, Product, and Global Security at the USPIS, discuss his organization's use of CERT-RMM, listen to the CERT podcast at https://resources.sei.cmu.edu/library/asset-view.cfm?assetID=34576.
More By The Author
More In Enterprise Risk and Resilience Management
Process and Technical Vulnerabilities: 6 Key Takeaways from a Chemical Plant Disaster
• By Daniel J. Kambic
PUBLISHED IN
Enterprise Risk and Resilience ManagementGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Enterprise Risk and Resilience Management
Process and Technical Vulnerabilities: 6 Key Takeaways from a Chemical Plant Disaster
• By Daniel J. Kambic
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
