How to Use the CMMC Assessment Guides
PUBLISHED IN
Enterprise Risk and Resilience ManagementTo receive certification under the Cybersecurity Maturity Model Certification (CMMC) 1.0 program, Department of Defense (DoD) contractors must successfully complete a third-party assessment. The DoD has released two CMMC assessment guides, the fundamental tools for both assessors and contractors to evaluate adherence to the CMMC framework. This blog post is intended for DoD contractors looking for additional clarification as they prepare for a CMMC assessment. It will walk you through the assessment guides, provide basic CMMC concepts and definitions, and introduce alternate descriptions of some practices. The goal is to help those unfamiliar with cybersecurity standards to better understand the CMMC practices and processes.
CMMC is a certification program to improve supply-chain security in the defense industrial base (DIB). Eventually, the DoD will require that all DIB companies be certified at one of the five CMMC levels, which include both technical security controls and maturity processes laid out in the Cybersecurity Maturity Model framework.
CMMC Assessment Guide - Level 1 and CMMC Assessment Guide - Level 3, released by the DoD in November 2020, are the defining documents for learning the details of CMMC certification. Assessors will use the guides during the certification process, and contractors can use them to prepare for it.
What happened to Level 2? It's considered a transitional level. Though it's recognized as a milestone for progress from Level 1 to Level 3, it's not expected to be a requirement in DoD contracts. CMMC also defines requirements for Levels 4 and 5, but those assessment guides haven't been published yet.
So, what level are you required to achieve? It all depends on what type of data your DoD contract requires you to use.
Public Information, Federal Contract Information, Controlled Unclassified Information
What This Means for You: Data Types Determine CMMC Level
Public Information - No CMMC Certification Required
Public information requires no special handling or controls, and CMMC doesn't address it. If you work with only public information in your DoD contract, you don't need CMMC certification. Public information is data identified as "Public Release Approved" or something similar, or it's unmarked information available from an uncontrolled, publicly available government source.
Federal Contract Information (FCI) - CMMC Level 1 Certification Likely
Federal contract information (FCI) is data not for public release. It's typically indicated in document markings or defined in the contract. FCI excludes basic accounting and transaction information required for invoicing and receiving payments. If your contract requires only FCI data, you'll probably need to achieve Level 1 CMMC certification, which includes 17 cybersecurity practices.
Controlled Unclassified Information (CUI) - At Least CMMC Level 3 Certification Required
Controlled unclassified information (CUI) is FCI that comes with additional guidance in the form of special safeguarding or handling controls. CUI should be clearly marked or clearly defined in your contract. You can find the most common additional guidance for CUI in National Institute of Standards and Technology (NIST) Special Publication 800-171. If your business with the DoD includes sharing and processing CUI data, you'll be required to achieve at least CMMC Level 3 certification, which requires compliance with all 133 practices and processes in Levels 1, 2, and 3:
- 17 Level 1 practices
- 55 Level 2 practices
- 2 Level 2 process-maturity requirements
- 58 Level 3 practices
- 1 Level 3 process-maturity requirement
Keep in mind that these are definitions and guidelines. Your DoD contracting officer is the ultimate authority for determining your CMMC certification level and how you should treat the data associated with your contract.
The assessment guides contain some opening sections that set the stage, followed by detailed entries for each practice and process in the CMMC model. We'll start by looking at the opening sections.
Introduction
The Assessment Guide Introduction section discusses DoD data types, describes the intended audience for the guide, and describes how the document is organized.
Assessment and Certification
The Assessment and Certification section is brief, but it touches on two important ideas. The first is that CMMC requirements are intended to apply to all contractor organizations, regardless of "size, constraints, or complexity." The other idea is the assessment scope. The assessment guide mentions it but defers any details until the next version of the guide. Pay attention to the definition of scoping as it's defined and published in future versions of the assessment guides. Understanding the scope of the assessment is fundamental for your assessment planning.
What This Means for You: Start Thinking About Assessment Scope
Even though the formal definition of CMMC scope is still being developed, you can get started with the following exercise. Create a picture of your network that identifies where FCI or CUI data is processed, transported, or stored. This picture will help determine the scope and boundaries of your network for the purpose of the assessment. Document these boundaries, then use the documentation as part of the discussions with your CMMC assessor. Check the documentation throughout the assessment planning and execution process to determine what's in or out of the scope of the assessment. This process helps ensure that you include only necessary locations, systems, and assets in the assessment.
Assessment Criteria and Methodology
The Assessment Criteria and Methodology section of the guides presents the assessment requirements that CMMC assessors follow. It defines the assessment objects (specifications, mechanisms, activities, and individuals) and methods (interview, examine, and test) that an assessor might require to verify implementation of a practice.
What This Means for You: The Evidence You'll Need
Be ready to demonstrate each practice using one or more of the three defined methods: interview, examine, and test. Determine which documents, screenshots, reports, or system outputs will help show your compliance with assessment objectives. Telling assessors about the implementation of practices may be the easiest way to communicate the evidence, but often it may not be sufficient. Also consider whether it makes sense to demonstrate a function by letting the assessor see it live.
Practice and Process Descriptions
Finally, the guides describe the CMMC practices and processes (referred to as "practices" going forward in this blog post). This section of the guides provides detailed information for assessing each CMMC practice beyond what the CMMC Model document provides. It gives the identifier and statement, assessment objectives, potential assessment methods and objectives, discussion and examples, and key references.

What This Means for You: Digging Into the Details
This section is where you can learn about each practice to determine what is required to implement it to an assessor's satisfaction. The guides use CMMC-specific notation and lots of material from technical cybersecurity standards. As an example, let's look at the first practice from the first domain, Access Control. In the Level 1 Assessment Guide, find the heading "Access Control (AC), Level 1 AC Practices" and follow along.
The practice identifier has three components separated by dots:
- two uppercase letters: the domain (there are 17)
- single-digit number: the CMMC level this practice is assigned to
- three-digit number: the unique number of the practice throughout the model
Those three-digit identifiers aren't always consecutive within a domain, and they sometimes make big jumps from one domain to the next. But don't worry: you can still use the three-digit number to identify any practice.

Following the practice identifier is the practice description: a sentence or two that concisely and formally defines the goal of the practice. Of the 130 practices in CMMC Levels 1-3, 110 come from NIST 800-171. Their practice descriptions come word-for-word from the NIST 800-171 standard. An additional 20 practices, also known as "delta practices," and 3 processes were developed for the CMMC.
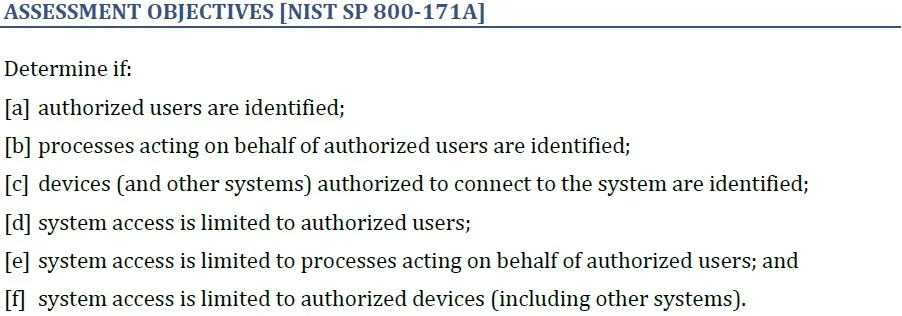
The assessment objectives are taken straight from NIST 800-171A. For the 23 practices and processes original to the CMMC, the Assessment Objectives section headers are followed by "[CMMC]."
The Assessment Objectives section spells out what an assessor will be looking at for a specific practice. The objectives are formatted as a list of outcomes identified by a bracketed lowercase letter used as reference in a later section of the practice description. The number of assessment objectives per practice varies from 1 to 10. All the objectives listed for a practice must be demonstrated to the assessor's satisfaction to pass that practice.
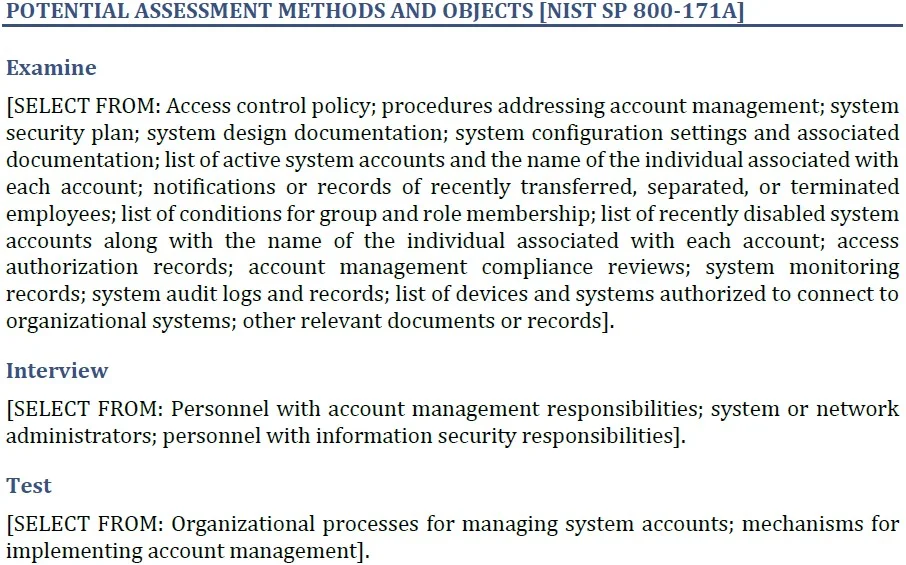
The Potential Assessment Methods and Objects section defines the artifacts and processes that an assessor might want to see and identifies which people in your organization, based on their responsibilities, an assessor might want to interview. For the practices that come from NIST 800-171, this section comes from NIST 800-171A. You should use these generic descriptions to determine which artifacts and specific people should be part of the assessment.

The Discussion section captures the cybersecurity principles associated with the practice. It either copies the practice explanation from NIST 800-171 or, for delta practices, copies from the CMMC model appendices.
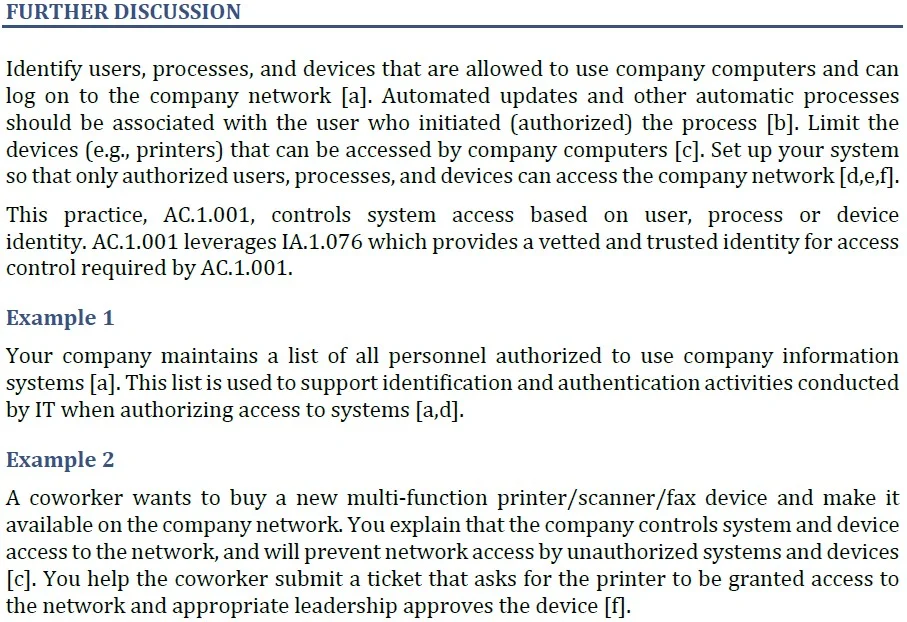
The Further Discussion section focuses on translating the technical description into operational terms. This section is not meant to tell you exactly how to implement the practice or cover all of the variations associated with the practice. Instead, it offers additional clarification of the practice and ties each relevant statement to the objectives from the Assessment Objectives section. (Remember the bracketed lowercase letters?)
Each practice has at least one example set in a generic company environment to make the practice more relatable. The examples are representative and aren't intended to prescribe how the practice should be implemented. The examples don't always include all the assessment objectives, either.

The Potential Assessment Considerations section provides statements or questions that may help an assessor determine if an organization is meeting the assessment objectives. The assessment objectives are also referenced here in brackets for clarity. As in the Further Discussion section and its examples, the information in this section doesn't prescribe a specific implementation or include every assessment objective.
In Other Words
Below are six examples of CMMC practices paired with a rephrasing intended to provide some additional clarification and explanation. You can find similar restatements of all 133 Level 1-3 practices and processes in a separate document, Overview of Practices and Processes of the CMMC Assessment Guides.
Identification and Authentication (IA)
Practice IA.3.083
Use multifactor authentication for local and network access to privileged accounts and for network access to non-privileged accounts.
In other words, require users to prove they are who they say they are using more than one technique: something you know (e.g., password), something you have (e.g., token), something you are (e.g., fingerprint).
Recovery
Practice RE.2.138
Protect the confidentiality of backup CUI at storage locations.
In other words, make sure the copies of the systems and data you create cannot be deleted or tampered with.
System and Communications Protection (SC)
Practice SC.1.175
Monitor, control, and protect organizational communications (i.e., information transmitted or received by organizational information systems) at the external boundaries and key internal boundaries of the information systems.
In other words, use available tools to create a protected barrier around your network and to separate internal portions of your network from each other.
Practice SC.3.177
Employ FIPS-validated cryptography when used to protect the confidentiality of CUI.
In other words, use NIST-approved cryptography to secure your sensitive data.
Practice SC.3.183
Deny network communications traffic by default and allow network communications traffic by exception (i.e., deny all, permit by exception).
In other words, block all incoming traffic, then allow traffic only after you are sure it is necessary to complete your mission.
Practice SC.3.184
Prevent remote devices from simultaneously establishing non-remote connections with organizational systems and communicating via some other connection to resources in external networks (i.e., split tunneling).
In other words, don't allow remote user systems to connect to your VPN and another network simultaneously. This practice will help prevent an attacker from another network from "passing through" your user's system to attack your network.
Further CMMC Guidance
See "In other words" phrasing for all 133 practices and processes from CMMC Levels 1-3 in the paper Overview of Practices and Processes of the CMMC Assessment Guides. Check out all of the SEI's CMMC guidance on our website: blog posts, podcasts, webinars, and more.
More By The Author
More In Enterprise Risk and Resilience Management
Process and Technical Vulnerabilities: 6 Key Takeaways from a Chemical Plant Disaster
• By Daniel J. Kambic
PUBLISHED IN
Enterprise Risk and Resilience ManagementGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Enterprise Risk and Resilience Management
Process and Technical Vulnerabilities: 6 Key Takeaways from a Chemical Plant Disaster
• By Daniel J. Kambic
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
