Combined Arms Cyber-Kinetic Operator Training
As cyber-physical systems continue to proliferate, the ability of cyber operators to support armed engagements (kinetic missions) will be critical for the Department of Defense (DoD) to maintain a technological advantage over adversaries. However, current training for cyber operators focuses entirely on the cyber aspect of operations and ignores the realities and constraints of supporting a larger mission. Similarly, kinetic operators largely think of cyber capabilities as a strategic, rather than a tactical resource, and are untrained in how to leverage the capabilities cyber operators can provide. In this blog post, I present Cyber Kinetic Effects Integration, also known as CKEI, which is a program developed at the SEI's CERT Division that allows the training of combined arms and cyber engagements in a virtual battlefield.
The Current State of Operations
The DoD has made it a priority to revamp its training approach to prepare warfighters for the new military theater: a combined arms and cyber engagement. "Fifth generation warfare is not just about fifth generation aircraft, such as F-22s and F-35s," said Capt. Neil Fournie, 414th Combat Training Squadron chief of Advanced Warfighting Division, in an article about the effort to combine air, space, and cyber Air Force training. "It's about building fifth-generation Airmen who understand how to combine air, space and cyber together to enable holistic battlespace dominance."
There is currently a divide, however, between warfighters who work solely in cyber-mission or cyber-protection teams and warfighters assigned to kinetic forces: units that operate machines and weaponry. Initiatives such as Cyber Support to Corps and Below have demonstrated a move toward blended missions, but the training and tools necessary for this new, combined mission space have not kept up.
The military has a long history of live, virtual, constructive training (known in the Mod/Sim community as LVC) for kinetic warfare. This kind of simulated warfare training exists for warfighters operating in the cyber environment, but it often focuses on the cyber environment exclusively. This single focus is at odds with the realities of cyber support in a real-world mission.
Training for Cross-Domain Requirements
The impact of cross-domain training cannot be overstated.
Consider a scenario in which a cyber operator accesses an enemy's command-and-control system to monitor enemy troop movements. If his connection passes through a fiber optic cable running across a bridge, the cyber operator must ensure that friendly forces do not damage the cable during normal operations, even if they must deny use of that bridge to the enemy.
Conversely, troops in theater must be able to properly communicate requirements to cyber operators. For example, they may need the power cut in a village to secure freedom of maneuver under the cover of darkness. Instead of using kinetic operations to take out powerlines, substations, or even a power plant, (that they may later have to rebuild), they can deploy a cyber action to neutralize that infrastructure temporarily, while minimizing the effect upon civilian populations.
The Cyber Kinetic Effects Integration (CKEI) system combines a mature cyber simulator and a mature kinetic simulator in a way that allows effects in one environment to propagate to the other. Stated more simply, CKEI provides training that combines cyber and kinetic missions in real time. This integration enables "whole-force training" in which cyber operators can learn to support live missions, while dealing with the realities of operating in contested networks and environments.
Within CKEI, systems can be attacked in cyberspace to produce a physical effect that provides a tactical advantage to the kinetic operators. Conversely, kinetic operators can damage or destroy systems within the kinetic simulator to deny cyber operators use of those systems in cyberspace.
To produce CKEI, we developed an easily extensible application programming interface (API) that bridges CERT's STEPfwd training environment (in which the cyber aspects of the mission reside) and a third-party kinetic mission training program. CKEI detects state changes in our cyber environment, such as when an alarm is triggered, or the configuration for a SCADA controller is changed, so it no longer produces power.
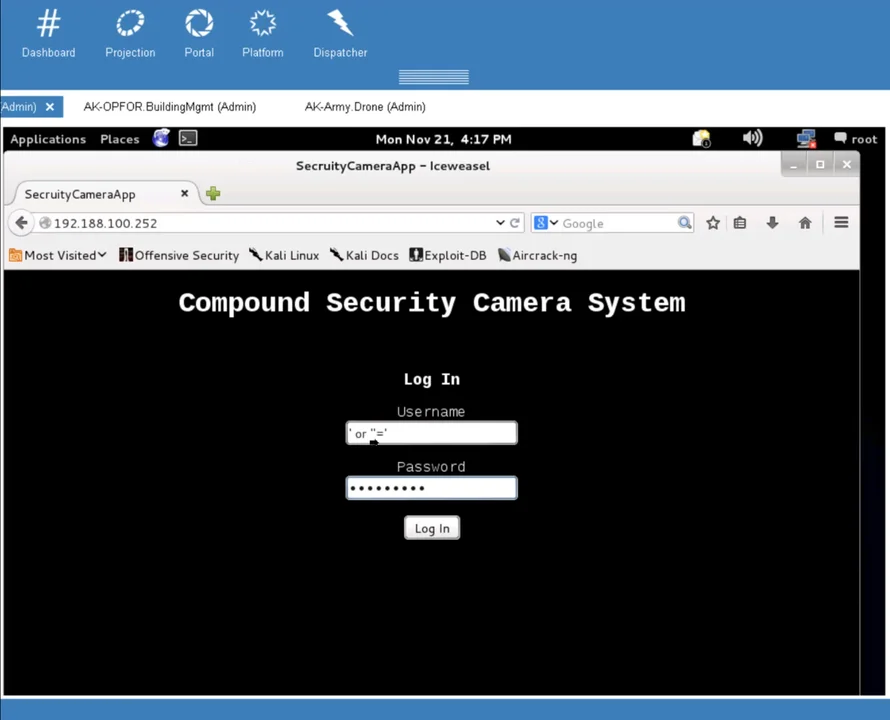
Here we see a cyber operator within the STEPfwd environment executing a basic SQL injection attack
CKEI then propagates those effects to the simulators using the API, which exchanges Java Script Object Notation (JSON)-formatted data structures that represent, by default, a system state value triple. This triple consists of
- the system element, which identifies the system whose state has changed,
- the state element, which identifies element(s) of the overall state that have changed, and
- the value element, which provides the new value(s)
This basic triple is common across all calls within the API, though they can be extended as needed to support additional functionality.
We have already integrated several different kinetic simulators using the CKEI interface, including Bohemia Interactive's VBS3, the aforementioned third-party kinetic mission training program.
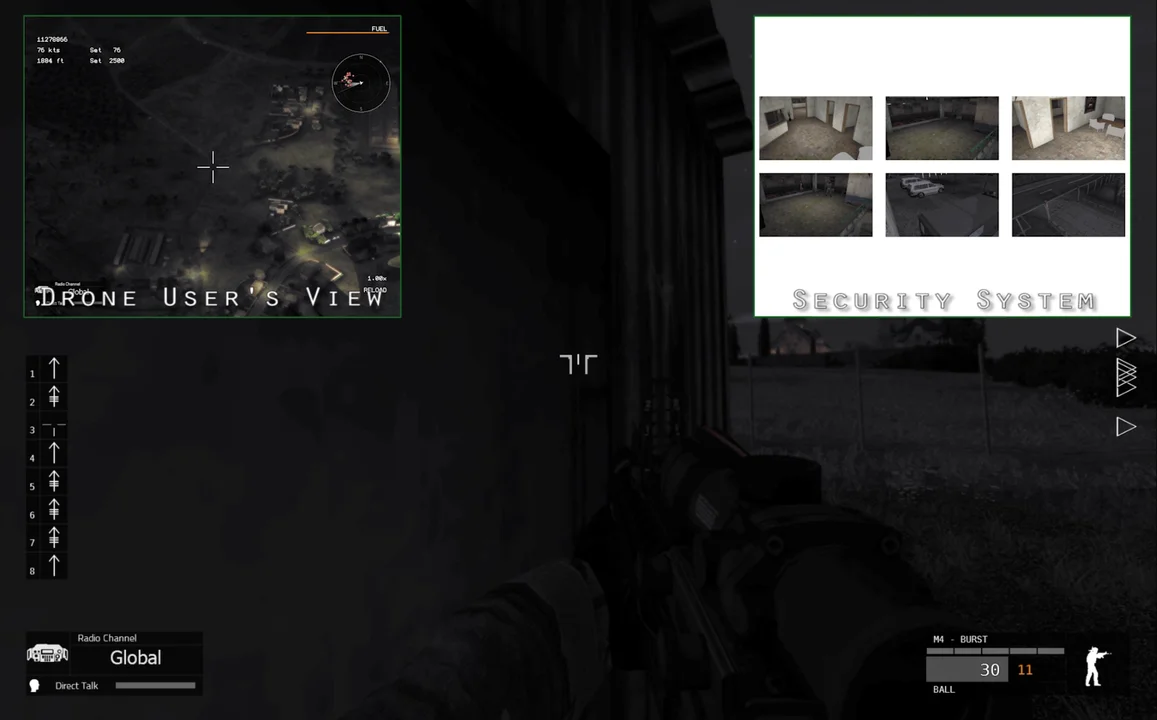
Mission
In the remainder of this blog post, I will take you through a mission concept scenario we created that is similar to what warfighters might encounter in the CKEI environment.
Proof of concept scenario. The scenario begins with a fictional island whose primary industry is tourism. The island has several luxury resorts along the coastline and a more impoverished local populace that lives inland. While the island country does not have a military, it has a police force. The island is located 400 nautical miles off the coast of Africa, but was considered relatively safe due to its location. Known pirates and insurgents in the area were limited to a 250 nautical mile range.
Triggering Event. A terrorist organization had captured a luxury yacht and used that yacht that to project force. The terrorists tied smaller craft to the yacht, put diesel canisters on the deck, and used the yacht to extend their range thus enabling them to reach the island. The island's police force, which was not prepared to defend itself from such an attack, lost control of the vessel to the terrorists. The terrorists took anything of value, including hostages. Those that would not cooperate were summarily executed.
In this scenario, the United States military continues to monitor the situation but has not yet become directly involved. The level of involvement changes after the terrorists post a video of a captured American reporter. The terrorists state in the video that if they don't receive a ransom of several million dollars within the next six hours the reporter will be murdered.
Our proof of concept mission. An eight-member special operations team is charged with going in, rescuing the hostage, and exfiltrating her from the island. Within a six-hour deadline, the team has to execute what is called a no-notice hasty op utilizing only the existing resources in the theater.
This special operations team is significantly outmanned and outgunned. Their only chance of success is to outsmart their adversaries--using cyber support. The hostage video is filmed in the courtyard of the island's central police compound. Intel indicates that the compound is being used as a local headquarters by the terrorists, so the special operations team suspects that is where the hostage is being held.
The compound is too large for the team to sweep and clear without risking the life of the hostage. To reach the compound, the team will have to move through an urban area defended by enemy checkpoints. Also, much of the countryside is guarded by enemy patrols.
Another challenge is the police complex itself, which has both searchlights and security alarm systems that may be triggered. The entire security complex has its own backup power generation capability.
Software and hardware at their disposal. The special operations team has at its disposal a ScanEagle unmanned aerial vehicle (UAV) that provides them with current intel via their communications back to base (and, of course, the cyber operators). The team is also equipped with tactical gear, including night vision goggles, assorted firearms and explosives, as well as bolt cutters.
Challenges to successful completion of the mission. The mission is designed to encourage the kinetic team and cyber operators to coordinate their efforts and rescue the hostage while overcoming challenges, including the following:
- Accessing the facility unnoticed by enemy checkpoints and patrols. This stealthy access is accomplished using intelligence provided by the UAV, which details the location of the checkpoints and allows the team to arrive at the target without encountering enemy forces.
- Defending against attacks on the friendly networks in the cyber environment. Failure to defend friendly networks can compromise or disable critical systems, such as the UAV feed--costing the kinetic team a valuable intelligence asset.
- Defending against attacks on communications infrastructure between the special operations team and personnel back at base, such as the commander, intel officer, and cyber operators. Any of these can also be attacked in our cyber environment. An inability to communicate with the troops in the field will deprive them of the ability to act on intel and make it extremely hard for them to get to the police facility without encountering enemy forces.
All of these attacks can be executed by either a live red team (opfor) or via automated attacks supported within the STEPfwd environment.
Mission support activities
As listed above, cyber operators must maintain the availability of services while kinetic operations are being conducted. While doing so, cyber operators must also support the kinetic operations in progress. Utilizing the resources at its disposal, the cyber team can gain network access and perform the following support activities:
- communicate with kinetic forces to inform tactical decision making with real-time information
- conduct a cyber attack on a local power substation to kill lights and disable scanning and detection devices
- hack into security camera feeds to obtain live views from the kinetic environment, such as the locations of the hostage and guards
- communicate information obtained from the live video feeds to commanders who then relay it to the special operations team in the field
- hack into the building management system and individually cut power to search lights, allowing the special operations team to enter the building, retrieve the hostage, and get out, while encountering minimal resistance
- conduct cyber attacks to prevent the alarm system from being triggered, or if triggered, from sounding
Our environment does not assume one correct way to attack these systems. We have created the systems in such a way that they actually operate like they would in the real world. For instance, when an entity in the kinetic simulator presses the alarm button, in the environment it sends a message to our system that effectively states, "This particular button has been pressed." When the button is pressed, a system within our cyber simulator sends network traffic to the central controller to tell it, "The alarm is being triggered."
That central controller then attempts to sound the alarm. If it succeeds, our system sends a message to the kinetic simulator letting it know which speakers are sounding right now. Anything that the cyber operators do in the environment that would disrupt any portion of this system will work as it would in the real world.
While we might have planned one way of compromising the alarm system, the cyber operators are free to devise something else. For example, we assumed the central alarm controller would be a primary target. Some teams instead chose to attack a router between the alarm trigger and central controller in a way that causes the router to drop packets. Such an attack prevents the network traffic from reaching the triggered system and thus the alarm would not sound.
We have not prescribed a specific path to success, rather we simply model all the systems involved so participants can determine their best path to success. Although an exercise in which the cyber team carries out all of its attacks, defenses, intelligence gathering, and guidance in support of the kinetic mission will result in the rescue of the hostage, we have found that the best training value is not when the cyber operators succeed but when they fail. By creating a system where failure has minimal consequences, and where the entire environment can be reset, we allow for teams to explore new tactics, techniques and procedures to determine what works best.
Wrapping Up and Looking Ahead
We recently tested CKEI with DoD cyber operators and, in August 2016, at a STEM event involving approximately 75 high school students. Details of this event are available here.
In late 2016, we exhibited CKEI at the ITSEC conference as a part of Operation Blended Warrior. During this event CKEI was integrated along with dozens of other simulations as a part of a large scale military simulation exercise.
In the coming year, we will continue this work through our follow on program, ACTS or Advanced Cyber Kinetics TTP (tactics, techniques, and procedures) Simulation. Through this work, we are expanding CKEI to allow for DoD doctrine development and mission rehearsal and iteration at low cost. We plan to do so by adding in-system mission planning and automated after-action review capabilities.
We welcome your feedback on this work in the comments section below.
Additional Resources
More By The Author
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedGet updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
