Bolstering Security with Cyber Intelligence
PUBLISHED IN
Situational AwarenessStephen Beck co-wrote this blog post.
A maxim for intelligence operators and military and special operations communities is "get off the X." The expression, once reserved for combat situations in reference to getting out of "the kill zone, point of attack, minefield, sniper crosshairs or other danger zone" has been adopted by the intelligence communities to convey the danger of a static approach to organizational security. As Michele Rigby Assad, a former intelligence officer in the CIA, explains, "the X refers to the site of an attack. This is the location in which the attackers have the greatest advantage because they control their environment... . From the target's perspective, the 'X' is the position of greatest vulnerability, where you have the least amount of control over the outcome of a situation." In this blog post, we explore how cyber intelligence principles can help organizations stay off the X and avoid specific locations where direct attack from nefarious cyber actors, terrorists, criminals, or other adversaries might occur when you are most vulnerable.
Intelligence operators and military and special operations teams prefer not to operate reactively in the field. Instead, they strive to gain advanced knowledge--through intelligence--to avoid potential X locations and situations. The discipline of intelligence is about identifying, collecting, processing, and analyzing disparate information that can enhance decision making. These teams do not rely only on basic security processes and procedures: they seek intelligence to better understand themselves and their adversary.
- Know yourself: Understand your personnel, the skills and responsibilities of team members, technology and other gear, transportation, communications, physical and virtual environment, and support lines, as well as the team's own potential vulnerabilities in the shared domain relative to an adversary's threat potential.
- Know the adversary: Understand the adversary's threat potential, or assessed intent and capability including, but not limited to, their attack methods, communications, transportation, type and level of sophistication pertaining to technology, and people and machines needed to conduct an attack.
Gaining this understanding is not easy. Learning is a continuous process whereby environments, situations, and capabilities change, are concealed, or are fabricated. As new intelligence is created and learning increases, however, military, intelligence operators and special operations teams incorporate intelligence to better protect themselves and to deliberately and methodically avoid known Xs and potential X locations.
Translation to Cyber Intelligence and Protecting Your Organization
Every day, organizations devote enormous resources (money, time, people, etc.) to avoid potential Xs, and simultaneously adversaries race to induce organizations and their employees to land on an X. As Ron Ross detailed in a NIST blog post, organizations commonly enhance their cybersecurity by following compliance regulations and performing cyber hygiene activities, such as "inventorying hardware and software assets; configuring firewalls and

other preventative commercial products; scanning for vulnerabilities; patching systems; and monitoring." Cyber hygiene practices, according to the SEI, help organizations "manage the most common and pervasive cybersecurity risks." These practices are critical. They must be continuous and formalized into organizational policy.
A challenge, however, is that too many organizations perform these practices reactively. There is insufficient strategic focus or effort to incorporate cyber intelligence to better protect against near and longer term threats (avoid current and potential Xs) and to seize business opportunities in and out of industry. When it comes to threats, cyber intelligence can help organizations better know themselves and adversaries by considering three factors, which we outline in our 2019 Cyber Intelligence Tradecraft Report on the State of Cyber Intelligence Practices in the United States:
1) Target / Organizational Exposure to the Threat: Maintain a deep understanding of your exposure to the threat due to vulnerabilities associated with people, an organization's cyber footprint which includes infrastructure, internet presence and physical and technological vulnerabilities.
2) Target / Organizational Impact of the Threat: Assess the organizational impact of the threat(s) which generally involve operational costs and strategic interests.
3) Threat Actor Potential: Understand the threat actor's potential to execute the threat by assessing intent and capability.
In our 2019 Cyber Intelligence Tradecraft Report on the State of Cyber Intelligence Practices in the United States, we included this image (View a full-sized version of the image here.) to show how organizations can holistically approach assessing threats.
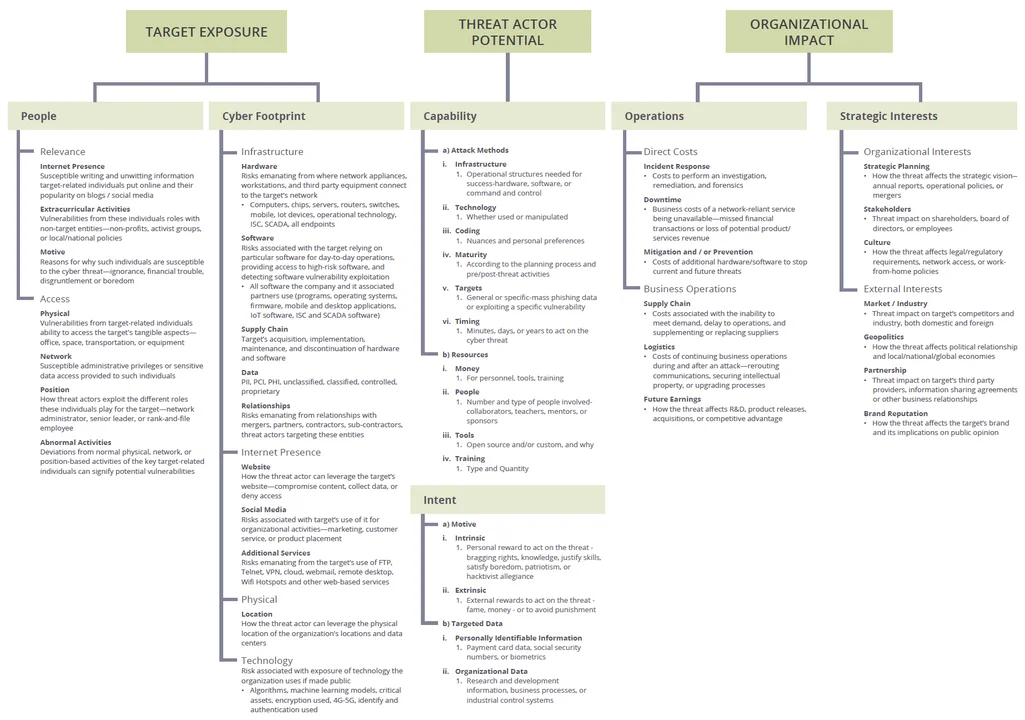
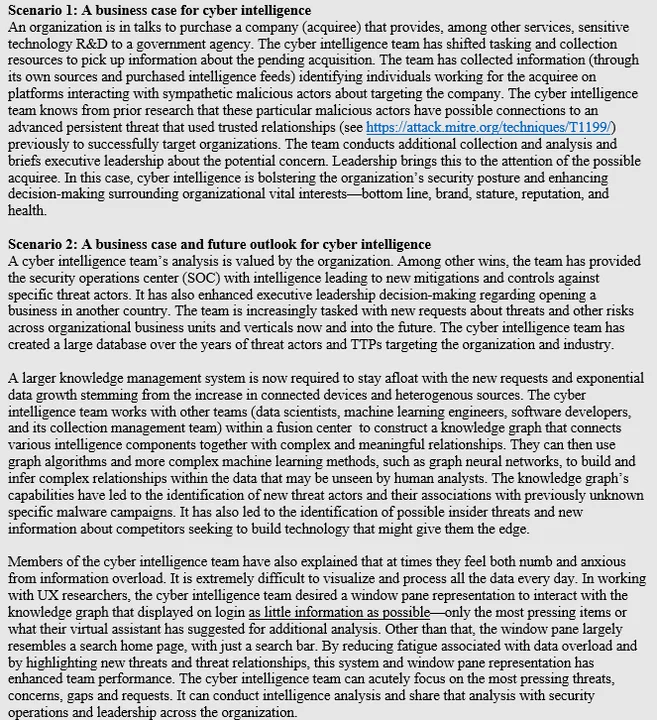
To produce the Cyber Intelligence Tradecraft report, we met with 32 organizations across the country. We interviewed cyber intelligence teams to learn how they perform cyber intelligence. We gathered information about how these teams protect their organizations against threats and how they provide intelligence to business leaders about these threats and larger strategic risks such as mergers and acquisitions. We also met organizations beginning to incorporate in-house machine learning capabilities to enable their cyber intelligence team to respond more efficiently to increasing intelligence product demands. To further highlight the importance of cyber intelligence, we expand on study observations to create two fictional scenarios for cyber intelligence. These fictional scenarios are intended to help organizations think about the utility of and possibilities of applying intelligence in the cyber domain to bolster an organization's holistic security posture.
Using Cyber Intelligence to Stay off the X
With cyber intelligence, organizational leaders have greater insight into the attack surface, critical assets and patent-pending technologies, leadership concerns about threats, threat actors keen on targeting their organization, threats targeting their supply chain and industry, and even emerging technologies such as 5G and artificial intelligence that could impact and provide opportunities for organizations. It enables leaders to role play as adversaries, determining the most likely attack vectors and evaluating corresponding defenses to ensure responses are not disorganized or chaotic. With all of this information, an organization is better positioned to not just react if or when it finds itself on the X, but rather anticipate where Xs may lie and to avoid them altogether.
Additional Resources
- View the podcast Cyber Intelligence: Best Practices and Biggest Challenges.
- Download the Cyber Intelligence Tradecraft Report - The State of Cyber Intelligence Practices in the United States.
- Download the Cyber Intelligence Tradecraft Report Executive Summary and Top Ten Findings.
- If you want to learn more about how cyber intelligence can help your organization avoid potential Xs, check out the Cyber Intelligence Tradecraft Report - The State of Cyber Intelligence Practices in the United States. Sponsored by the U.S. Office of the Director of National Intelligence, this report was published in May 2019 and highlights best practices and common challenges of organizations across government, industry, and academia performing cyber intelligence. The report offers a framework for cyber intelligence and gives actionable steps that organizations can take to build a high-performing cyber intelligence capability. Lastly, the report includes three implementation guides organizations can use to incorporate machine learning, IoT, and cyber threat frameworks into their cyber intelligence practices.
More By The Authors
More In Situational Awareness
PUBLISHED IN
Situational AwarenessGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Situational Awareness
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed


