Archive: 2020
Ransomware as a Service (RaaS) Threats
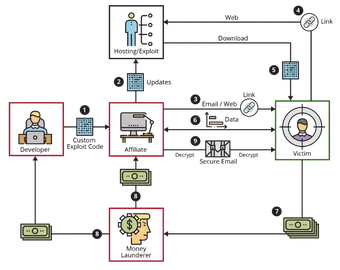
This blog post explores the economics behind why ransomware remains a top tool for cybercrime and presents the current active ransomware variants that utilize ransomware as a service (RaaS), a …
Read More•By Marisa Midler
In CERT/CC Vulnerabilities

Three Places to Start in Defending Against Ransomware
Learn three initial efforts for defending against ransomware in this informative SEI Blog post.
Read More•By Timothy J. Shimeall
In CERT/CC Vulnerabilities

Verifying Timing in Undocumented Multicore Processors
Discover a project that verifies software timing on multiple cores without shared hardware resource information, enabling faster upgrades in this SEI Blog.
Read More•By Bjorn Andersson

Shifting from Software Sustainment to Software Engineering in the DoD
This post describes key issues that should be addressed by sustainment organizations, sustainment funding activities, and other stakeholders to make this transition successful.
Read More•By Thomas Evans, Michael J. Gagliardi, Mena Kostial, Nicholas Reimer, Douglas Schmidt (Vanderbilt University)
In Software Engineering Research and Development


Show Me Agility: Agile Strategy Execution
This SEI Blog post discusses the use of data and the concept of Agile strategy as a role-based enterprise capability for effective execution.
Read More•By Linda Parker Gates
In Agile

Cat and Mouse in the Age of .NET
This SEI Blog post explores evolving .NET threat landscape with challenges faced by red and blue teams and suggests ways to stay ahead of attackers.
Read More•By Brandon Marzik
In CERT/CC Vulnerabilities

What Is Digital Engineering and How Is It Related to DevSecOps?
Discover how Digital Engineering intersects with DevSecOps in this informative SEI Blog article.
Read More•By David James Shepard, Julia Scherb
In DevSecOps


Mission-Based Prioritization: A New Method to Sequence Features, Capabilities, and Epics
Learn a new method to prioritize an Agile backlog using mission-based parameters in this informative SEI Blog post.
Read More•By Keith Korzec
In Agile

3 Ransomware Defense Strategies
This SEI Blog post covers strategies to mitigate RDP attacks & software vulnerabilities, and how to protect against data exfiltration after phishing defense.
Read More•By Marisa Midler
In Reverse Engineering for Malware Analysis

A Public Repository of Data for Static-Analysis Classification Research
This blog post describes a new repository of labeled data that CERT is making publicly available for many code-flaw conditions. Researchers can use this dataset along with the associated code …
Read More•By Lori Flynn
In Secure Development

SEI Blog Archive
Recent
Year