- Agile
- Artificial Intelligence Engineering
- CERT/CC Vulnerabilities
- Cloud Computing
- Continuous Deployment of Capability
- Cyber-Physical Systems
- Cybersecurity Center Development
- Cybersecurity Engineering
- Cyber Workforce Development
- Edge Computing
- Enterprise Risk and Resilience Management
- Innovative Acquisition
- Insider Threat
- Model-Based Systems Engineering
- Quantum Computing
- Reverse Engineering for Malware Analysis
- Secure Development
- Situational Awareness
- Software Architecture
- Software Engineering Research and Development
- Technical Debt
The Essential Role of AISIRT in Flaw and Vulnerability Management
The SEI established the first Artificial Intelligence Security Incident Response Team (AISIRT) in 2023. This post discusses AISIRT's role in the coordination of flaws and vulnerabilities in AI systems.
Read More•By Lauren McIlvenny, Vijay S. Sarvepalli
In Artificial Intelligence Engineering


Enhancing Machine Learning Assurance with Portend
This post introduces Portend, a new open source toolset that simulates data drift in machine learning models and identifies the proper metrics to detect drift in production environments.
Read More•By Jeffrey Hansen, Sebastián Echeverría, Lena Pons, Gabriel Moreno, Grace Lewis, Lihan Zhan
In Artificial Intelligence Engineering


Cybersecurity of Logistics Decision Models
Goods, services, and people simply cannot get to where they are needed without effective logistics. In this blog post we will focus on cyber attacks to logistics decision models.
Read More•By Clarence Worrell, Lauren Hoge
In Cyber-Physical Systems


The DevSecOps Capability Maturity Model
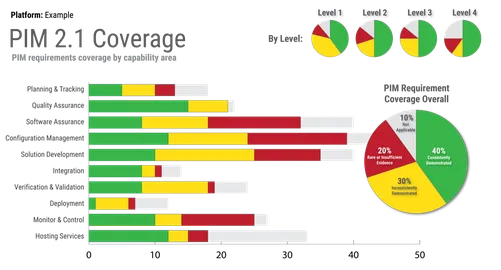
Implementing DevSecOps can improve multiple aspects of the effectiveness of a software organization and the quality of the software for which it is responsible.
Read More•By Timothy A. Chick, Brent Frye, Aaron K. Reffett
In Continuous Deployment of Capability


Detection and Repair: The Cost of Remediation
This year, we plan on making some exciting updates to the SEI CERT C Coding Standard. This blog post is about one of our ideas for improving the standard.
Read More•By David Svoboda
In Secure Development

Perspectives on Generative AI in Software Engineering and Acquisition
It is essential that software and acquisition professionals learn how to apply AI-augmented methods and tools in their workflows. SEI researchers offer their perspectives on this topic.
Read More•By Anita Carleton, James Ivers, Ipek Ozkaya, John E. Robert, Douglas Schmidt (William & Mary), Shen Zhang
In Software Engineering Research and Development


Protecting AI from the Outside In: The Case for Coordinated Vulnerability Disclosure
This post highlights lessons learned from applying the coordinated vulnerability disclosure (CVD) process to reported vulnerabilities in AI and ML systems.
Read More•By Allen D. Householder, Vijay S. Sarvepalli, Jeff Havrilla, Matt Churilla, Lena Pons, Shing-hon Lau, Nathan M. VanHoudnos, Andrew Kompanek, Lauren McIlvenny
In Artificial Intelligence Engineering


Introducing MLTE: A Systems Approach to Machine Learning Test and Evaluation
Machine learning systems are notoriously difficult to test. This post introduces Machine Learning Test and Evaluation (MLTE), a new process and tool to mitigate this problem and create safer, more …
Read More•By Alex Derr, Sebastián Echeverría, Katherine R. Maffey (AI Integration Center, U.S. Army), Grace Lewis
In Artificial Intelligence Engineering


Cyber-Informed Machine Learning
This blog post proposes cyber-informed machine learning as a conceptual framework for emphasizing three types of explainability when ML is used for cybersecurity.
Read More•By Jeffrey Mellon, Clarence Worrell
In Cybersecurity Engineering


Introducing the Insider Incident Data Exchange Standard (IIDES)
Capturing and sharing information about insider incidents is a challenge. This post introduces the Insider Incident Data Exchange Standard (IIDES) schema for insider incident data collection.
Read More•By Austin Whisnant
In Insider Threat

Explore Topics
- Agile
- Artificial Intelligence Engineering
- CERT/CC Vulnerabilities
- Cloud Computing
- Continuous Deployment of Capability
- Cyber-Physical Systems
- Cybersecurity Center Development
- Cybersecurity Engineering
- Cyber Workforce Development
- Edge Computing
- Enterprise Risk and Resilience Management
- Innovative Acquisition
- Insider Threat
- Model-Based Systems Engineering
- Quantum Computing
- Reverse Engineering for Malware Analysis
- Secure Development
- Situational Awareness
- Software Architecture
- Software Engineering Research and Development
- Technical Debt
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedGet updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed