Software Assurance
Blog Posts
Taking Up the Challenge of Open Source Software Security in the DoD
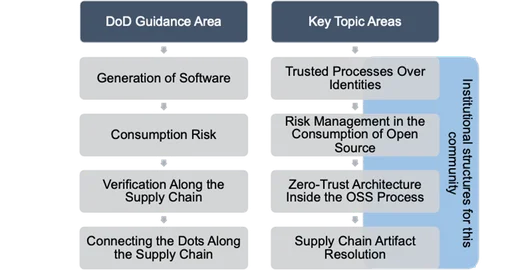
This post describes a workshop hosted by the SEI to start a conversation to elevate the trustworthiness of free and open source software, particularly in DoD settings.
• By Scott Hissam
In Secure Development

Six Dimensions of Trust in Autonomous Systems
This post chronicles the adoption and growth of autonomous systems and provides six considerations for establishing trust.
• By Paul Nielsen
In Software Engineering Research and Development

Six Acquisition Pathways for Large-Scale, Complex Systems
How to map technical reference frameworks (TRFs) to the pathways that compose the DoD’s Adaptive Acquisition Framework (AAF)
• By Douglas Schmidt (Vanderbilt University), Nickolas Guertin
In Software Architecture


Toward Technical Reference Frameworks to Support Large-Scale Systems of Systems
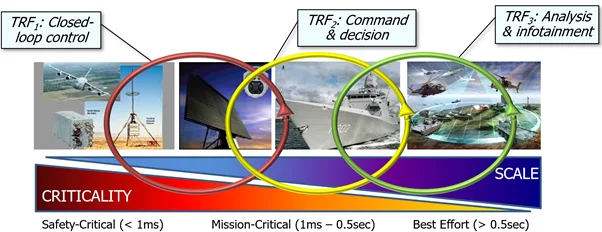
Strategies for creating architectures for large-scale, complex, and interoperable systems of systems that are composed of functions covering a broad range of requirements.
• By Nickolas Guertin, Douglas Schmidt (Vanderbilt University)
In Software Architecture


Safety Assurance Does Not Provide Software Assurance
This SEI Blog on cybersecurity in cyber-physical systems (CPS), shows how safety evaluations fail to protect against cyber threats.
• By Mark Sherman
In Cyber-Physical Systems

Anti-Tamper for Software Components
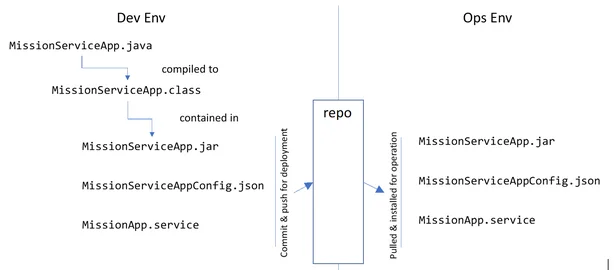
This post explains how to identify software components within systems that are in danger of being exploited and that should be protected by anti-tamper practices.
• By Scott Hissam
In Secure Development

7 Quick Steps to Using Containers Securely
The use of containers in software development and deployment continues to trend upwards. There is good reason for this climb in usage as containers offer many benefits....
• By Tom Scanlon, Richard Laughlin


Data-Driven Management of Technical Debt
Learn about the SEI's work on technical debt analysis techniques and practices to help software engineers manage its impact on projects in this SEI Blog post.
• By Ipek Ozkaya, Robert Nord
In Technical Debt


Automated Assurance of Security-Policy Enforcement In Critical Systems
As U.S. Department of Defense (DoD) mission-critical and safety-critical systems become increasingly connected, exposure from security infractions is likewise increasing....
• By Peter H. Feiler

Seven Principles for Software Assurance
This SEI Blog post presents seven principles for achieving software assurance: stakeholder involvement, risk management, continuous monitoring, and more.
• By Nancy R. Mead
