Benefits and Challenges of SOAR Platforms
Network and defense analysts are facing increasing numbers of security alerts and, as a result of fielding those alerts, burnout. Dark Reading reported that the average security operations center (SOC) receives 10,000 alerts each day from layer upon layer of monitoring and detection products. While the cyber threat landscape is marked by an upward trending number of actors, network and defense analysts must also contend with ever-increasing numbers of false positives (sometimes at rates as high as 80 percent). Due to resource constraints on already overwhelmed analysts, many alerts are ignored, and, according to a recent report, less than 10 percent of alerts are actively investigated.
Security orchestration, automation, and response (SOAR) platforms, a term first coined by Gartner, refers to "technologies that enable organizations to collect inputs monitored by the security operations team. For example, alerts from the SIEM system and other security technologies -- where incident analysis and triage can be performed by leveraging a combination of human and machine power -- help define, prioritize and drive standardized incident response activities. SOAR tools allow an organization to define incident analysis and response procedures in a digital workflow format." It enables already overwhelmed network and defense analysts to compile threat-related data from various disparate sources and then use machine learning to automate responses to low-level threats. SOAR was one of the initial products aimed at easing the burden not only on security operations center (SOC) analysts, but on other security professionals such as security information and event management (SIEM) operators, threat hunters, and compliance managers. In this blog post, we introduce and analyze SOAR platforms, which help analysts deal with alert fatigue.
What Is SOAR?
The concepts of security orchestration, automation, and response were not new, but 2015, when Gartner coined the SOAR term, seems to be the first time the concepts were discussed as a category of tools where all four functions are part of a single platform. SOAR also incorporates threat intelligence by combining security orchestration and automation (SOA), security incident-response platforms (SIRPs), and threat-intelligence platforms (TIPs). Gartner defines SOAR platforms as
technologies that enable organizations to collect inputs monitored by the security operations team. For example, alerts from the SIEM system and other security technologies -- where incident analysis and triage can be performed by leveraging a combination of human and machine power -- help define, prioritize and drive standardized incident response activities. SOAR tools allow an organization to define incident analysis and response procedures in a digital workflow format.
The machine assistance, which includes automation, machine learning, and artificial intelligence functionality, can encompass many facets of cybersecurity and policy as SOAR incorporates all of the concepts listed above. SOAR platforms will plug into available data pipelines and network-security/management tool suites, such as SIEMS, firewalls, and threat-intelligence APIs. Orchestration is achieved with this access, allowing the SOAR platform to perform coordination of security actions to support a process or workflow across multiple tool suites. Further, it helps add automation for security teams through the creation of playbooks, as detailed in the February 2018 Gartner report Preparing Your Security Operations for Orchestration and Automation Tools and in the image below:
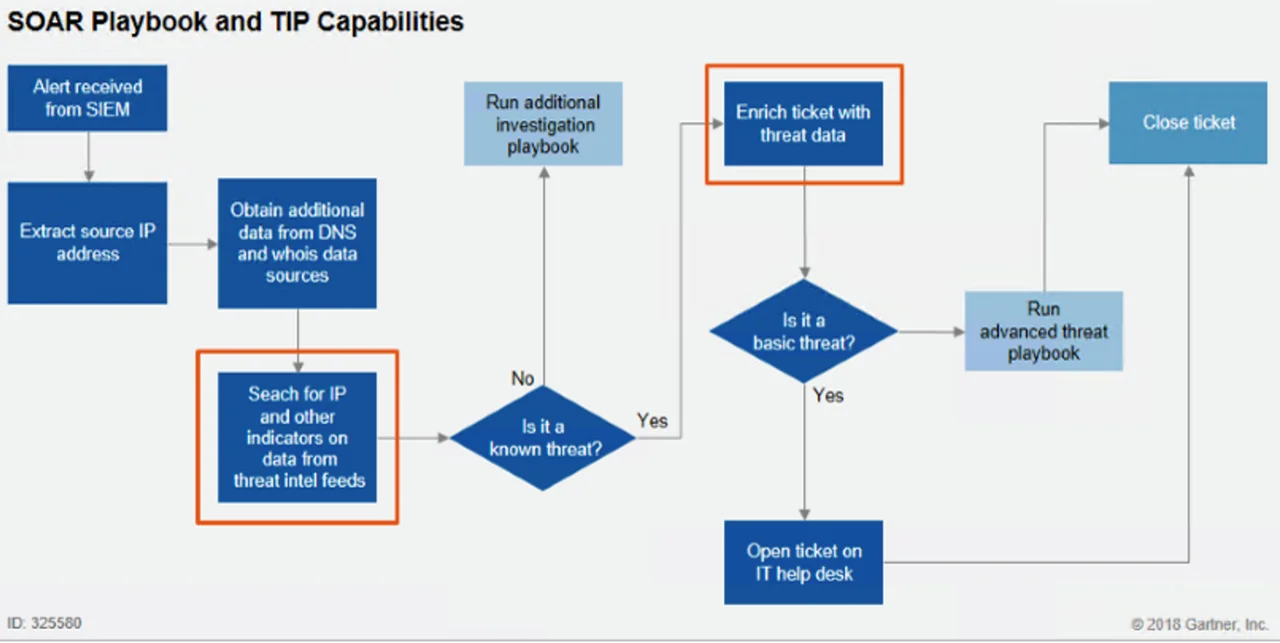
A playbook details a workflow or processes of the security team, usually in a graphical interface, to add automation where possible in the processes. It is important to note that the goal of SOAR is not to fully automate the workflow of an SOC, but to save the time of security professionals by automating simple redundant processes in their workflow. Additionally, SOAR platforms can provide methods to track incidents, events, cases, or tickets. Overall, SOAR platforms add machine assistance to security orchestration, automation, and response.
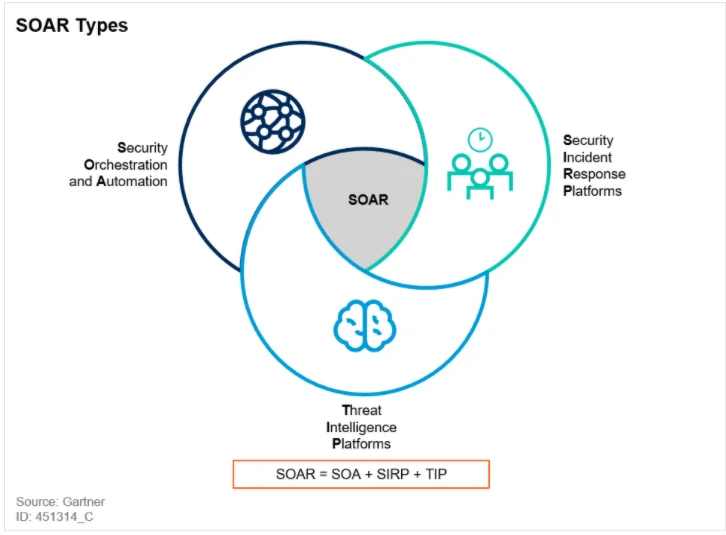
Four Engines of SOAR
Gartner identifies four engines that drive SOAR platforms, adding further context to what SOAR does. The four engines are workflow and collaboration, ticket and case management, orchestration and automation, and threat intelligence management.
The workflow-and-collaboration engine requires documentation of workflows or processes, but once configured, it will help security teams apply detailed workflows consistently. These workflows can then be organized and standardized so that all of the necessary professionals, including SOC analysts, IT analysts, quality assurance staff, are given their part at the appropriate time with appropriate context. This is a large improvement over previous methods for handling workflows and collaboration, such as undocumented knowledge, which can lead to gaps in analysis and team disorganization.
Ticket and case management identifies SOAR's ability to address incident case management. This engine provides security teams with the SIRP functionality to track cases, document processes, manage knowledge, and report compliance issues. The benefit over having a separate non-SOAR SIRP is that the case management is tied into the rest of the engines on the SOAR platform. The information within the case-management system can benefit other engines by making information or processes available, but it will also benefit from information from other sections to enrich case-relevant information. Additional separation from typical IT service management (ITSMs), such as JIRA or ServiceNow, allows for further compartmentalization of security-incident-related information from lower risk IT information.
Orchestration and automation connect in a SOAR platform to bring greater efficiency and efficacy to security teams and other users. As mentioned previously, SOAR will connect into other technologies, such as SIEMS or firewalls, to orchestrate--and through that orchestration, to automate. It is important to note that not all SOAR vendors use the same connection or have the same compatibility. Once connected, SOAR can automate security tasks in the various tools within a security network, or add a layer of abstraction where the security professional is interacting with SOAR and not necessarily the tool from which it is consuming data. This layer of abstraction can help security teams streamline training and processes as more functionality is held under the single SOAR graphical interface, requiring a security professional to learn one tool instead of a number of different tools.
The final engine, threat-intelligence management, performs many of the same functions as regular threat-intelligence platforms (TIPs) in how machine-readable threat intelligence is leveraged. SOARs connectivity again is a force multiplier, allowing for the aggregation, deduplication, and distribution of threat-intelligence feeds. Given SOAR's connection with other security tools, threat intelligence can be rapidly pushed downstream to a SIEM or firewall.
Limitations
A number of limitations and dependencies have emerged with SOAR platforms that could reduce their overall viability in enterprise security.
The biggest misperception is that SOAR platforms could ultimately replace security professionals. SOAR is meant to be a force multiplier for security teams, allowing them to work efficiently and effectively, but does not replace the human component. Further, the dependencies require more effort up front before that greater efficiency can be realized. First, the security team must have experienced professionals who already have or are able to create detailed workflows of their processes. Without this documentation, a team cannot operationalize SOAR in a completely beneficial way. If the professionals on the team are less experienced, they are likely not to understand the workflow and processes deeply enough to create worthwhile documentation from which SOAR will operate. Additionally, they must understand their environment enough to collect and understand operational metrics. If a security team does not know how to collect metrics to measure their effectiveness, it will be difficult to measure the actual benefit the organization is receiving from a SOAR platform. Without these metrics, it will be difficult to change how SOAR is set up in the enterprise for maximum benefit to the organization.
A final challenge is that the SOAR platform must be deployed to the enterprise and connected to the various other applications and technologies, a complex undertaking. An organization must have personnel with the necessary technical skills to deploy and maintain the platform. The applications and technologies used by the enterprise must also support or be supported to integrate into a SOAR platform. Because one of SOAR's greatest strengths is to connect to and orchestrate other technologies, each technology that is unable to be integrated hampers the benefits of deploying SOAR.
AIOps and SOAR
Artificial intelligence for IT operations (AIOps) solutions aggregate data to provide automation and analysis of IT tasks. These solutions go beyond the level of automation provided by SOAR platforms, but are ultimately aided by the aggregation that SOAR platforms provide. The presence of a SOAR platform provides greater opportunity for an enterprise to harness real machine learning and higher levels of automation that are present in AIOps. Given this relationship, it is possible that AIOps will be bolted on to the security platform suite of large vendors, such as IBM, Splunk, and others, just as they have done with SOAR. The dependencies required to achieve automation and machine learning for this space can be enhanced if the vendors continue to engineer solutions that complement and feed each other. Yet, in the end we will have many different security suites where enterprise customers will be even more dependent on the vendor, probably with less visibility into how the platforms are actually engineered.
Are SOAR Platforms a Necessary Burden?
As an emergent technology, SOAR platforms continue to grow in the field of enterprise security, but given their complexity, it is unclear if they will ever become as ubiquitous as other security technologies. Large vendors and enterprise customers continue to invest in and expand this space. SOAR offers answers to many problems that security teams currently have in terms of oversaturation of data and tool suites. SOAR platforms have also helped security professionals orchestrate and automate alerts, providing some small reduction of alert fatigue.
Yet, the complexity needed to achieve this orchestration and automation can be a burden, potentially to the point of hindering the overall usefulness of the platform. It is no small feat to deploy, connect, and maintain a SOAR platform, but those organizations with the requisite experience and time would see improved efficiency.
Additional Resources
Read the SEI blog post Situational Awareness for Cybersecurity Architecture: Tools for Monitoring and Response.
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedGet updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
