Ransomware as a Service (RaaS) Threats
PUBLISHED IN
CERT/CC VulnerabilitiesRansomware continues to be a severe threat to organizations, and the threat is growing. Ransomware attacks are on the rise and a report from the Beazley Group shows ransomware attacks have increased by 25 percent from Q4 2019 to Q1 2020. The monetary value of the average ransom payment has also significantly increased. From Q3 2019 to Q4 2019 the average ransom payment increased from $41,198 to $84,116, a 104 percent increase according to a January 2020 Coveware report. Moreover, according to an April 2020 Coveware report, during Q1 of 2020 the average ransom payment was $111,605, which is an increase of more than 33 percent from Q4 of 2019. This blog post explores the economics behind why ransomware remains a top tool for cybercrime and presents the current active ransomware variants that utilize ransomware as a service (RaaS), a change in the ransomware business model that could lead to a significant upswing in ransomware activity.
Ransomware is malware that uses strong encryption to lock and imprison targeted files, making decryption practically impossible without a key or hacking potential encryption implementation flaws. Ransomware attacks are largely opportunistic and typically infect a myriad of easy targets in the hopes of collecting the highest financial reward. After an attacker uses ransomware to encrypt a victim's data, the attacker sends a ransom note demanding payment for a decryption tool to recover the data held hostage. Unless organizations have a contingency plan to recover their data, or the encrypted files have no value, the victims end up paying the ransom or lose their files. It is worth noting that even if the victims pay the ransom, they may not regain access to their data. The FBI recommends against paying the ransom to the attackers and the U.S. Treasury Department is now exploring financial penalties to organizations who pay a ransom to recover their data.
Active Ransomware Variants
Table 1 below shows the top 10 most active ransomware variants in Q1 2020.
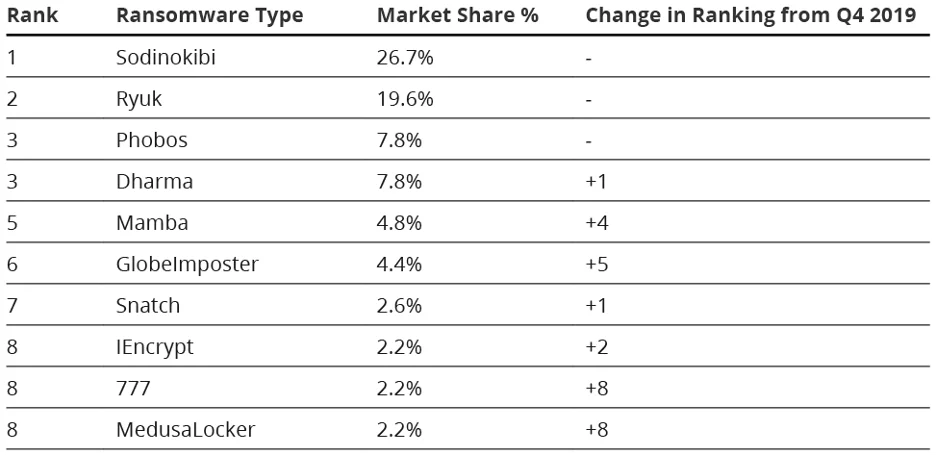
Of the top 10 active ransomware variants listed above, Sodinokibi, Phobos, Dharma, and GlobeImposter are known to use the ransomware as a service (RaaS) business model, which is explained in the paragraph below. At the RSA Conference 2020, FBI Special Agent Joel DeCapua presented research tracking Bitcoin wallets associated with ransomware variants that found victims paid $140 million in ransoms from 2013 to 2019. According to DeCapua, Dharma, Sodinokibi, Phobos, and GlobeImposter are within the top ten variants having collected $24.48 million, $6.63 million, $5.30 million, and $3.26 million respectively in ransom payments. This indicates that the RaaS model is an effective strategy to collect ransoms. It is worth noting that the actual amount of payments collected during the six years is likely larger than what has been recorded because the FBI did not have access to all the ransom notes and Bitcoin wallets.
What is Ransomware as a Service (RaaS)?
RaaS is a new business model for ransomware developers. Like software as a service (SaaS), the ransomware developers sell or lease their ransomware variants to affiliates who then use them to perform an attack. The RaaS business model makes ransomware usable by non-computer-savvy persons. Figure 1 below portrays a workflow for an attack using an RaaS platform; this figure is featured in the SEI white papers Current Ransomware Threats and An Updated Framework of Defenses Against Ransomware. The following steps occur in this workflow:
- The ransomware developer creates custom exploit code that is then licensed to a ransomware affiliate for a fee or share in proceeds from the attack.
- The affiliate updates the hosting site with the custom exploit code.
- The affiliate identifies and targets an infection vector and delivers the exploit code to the victim (e.g., via malicious email).
- The victim clicks the link or goes to the website.
- The ransomware is downloaded and executed on the victim's computer.
- The ransomware encrypts the victim's files, identifies additional targets on the network, modifies system configurations to establish persistence, disrupts or destroys data backups, and covers its tracks.
- The victim receives a ransom note and is instructed to pay ransom with untraceable funds, typically cryptocurrency.
- A money launderer will move the money through multiple transformations to obscure the identities of the ransomware affiliate and developer.
- The ransomware affiliate may send a decryptor to the victim once a ransom payment has been received. The affiliate may make additional demands on the victim or do nothing at all and leave the victim with encrypted files.
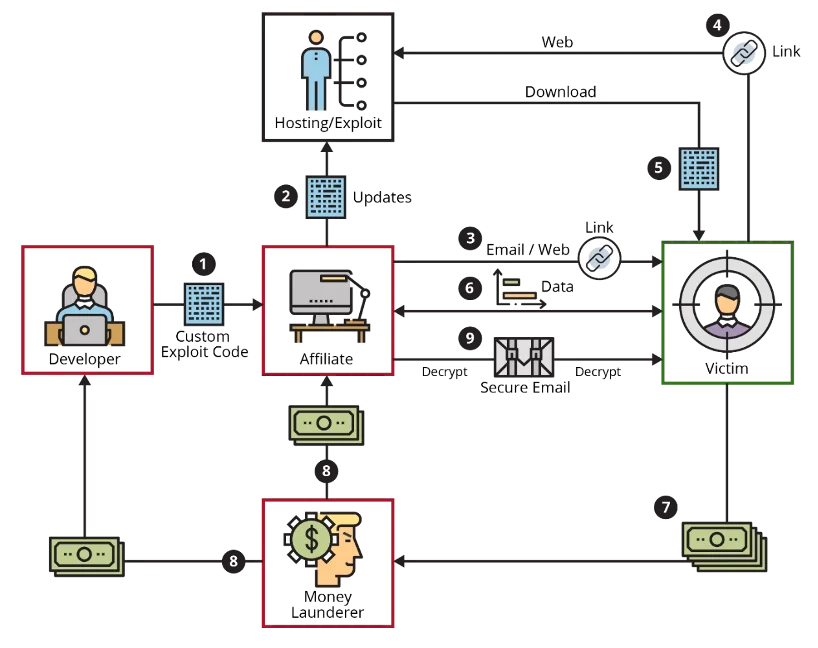
Figure 1: Ransomware as a Service Workflow as featured in Current Ransomware Threats and An Updated Framework of Defenses Against Ransomware
Why does RaaS matter?
Ransom payments are becoming more expensive, and we can assume that the profitability of ransomware is increasing for attackers. With RaaS, ransomware is no longer limited to the developers who create it. Ransomware developers now sell their product to ransomware affiliates who use it to extort organizations. RaaS decreases the risk for ransomware developers since they do not have to execute attacks.
For ransomware affiliates, RaaS reduces the cost to perform attacks since they can use prebuilt ransomware. RaaS expands the ransomware threat landscape because affiliates no longer need to develop their own variant to perform an attack and make money. For ransomware developers, RaaS can be as profitable as direct ransom payments since both developers and affiliates get a percentage of the paid ransoms, and the ransomware is affecting more targets and occurring more often.
A Persistent Problem
The ransomware threat is growing. Ransomware attacks are on the rise, and the monetary value for ransomware payments is rapidly increasing. The RaaS business model is gaining popularity with ransomware developers as indicated by the increasing number of ransomware variants using the model. This increase in RaaS support creates more opportunities for external affiliates to use ransomware, further expanding the threat landscape to organizations. Overall, ransomware will remain a problem for the foreseeable future, so it is imperative for organizations to take preventative action to protect themselves.
A future post from my colleague Tim Shimeall will discuss where organizations should start to defend themselves from ransomware, and a third post will focus on prioritized actions to take for awareness and mitigation of these threats.
Additional Resources
The SEI white paper An Updated Framework of Defenses Against Ransomware by Timothy Shimeall and Timur Snoke, which is loosely structured around the NIST Cybersecurity Framework, seeks to frame an approach for defending against Ransomware-as-a-Service (RaaS) as well as direct ransomware attacks.
The SEI white paper Current Ransomware Threats by Marisa Midler, Kyle O'Meara, and Alexandra Parisi discusses ransomware, including an explanation of its design, distribution, execution, and business model.
The SEI blog post Ransomware: Best Practices for Prevention and Response by Alexander Volynkin, Angela Horneman, and Jose Morales outlines several best practices for prevention and response to a ransomware attack.
More By The Author
More In CERT/CC Vulnerabilities
PUBLISHED IN
CERT/CC VulnerabilitiesGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In CERT/CC Vulnerabilities
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
