Network Segmentation: Concepts and Practices
Imagine a home with only a single large space containing all of your important things, arranged for your convenience. Now imagine someone breaking into it. How safe are your important things? Many organizations implement their networks the same way. By seeking easy and uncomplicated network management--or simply because they don't know better--many organizations can end up with hundreds or thousands of systems connected in a single, massive network. This arrangement can lead to havoc if the network falls victim to attack or even unintentional error. In this blog post, we review the basics of network segmentation and describe how organizations should implement it as an ongoing process.
Flat Networks vs. Segmented Networks
"Flat network" refers to an architecture where all devices can connect to each other without going through any other hardware, as shown in Figure 1. Flat networks provide fast and reliable connectivity for all connected devices, and security efforts generally concentrate on isolating internal networks from external networks. This traditional approach, however, is no longer satisfactory to secure modern enterprises' complex web of interconnected systems and organizations. Flat network architecture has led to high-profile cybersecurity incidents like the WannaCry ransomware attack and breaches at large financial services firms.
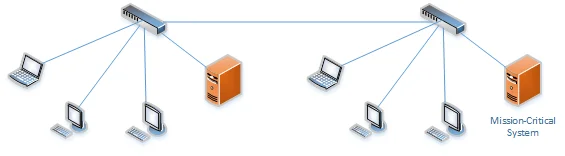
The key vulnerability of a flat network design is that once attackers successfully compromise the network, they might be able to move laterally, from one system to another, potentially gaining access to more sensitive systems.
The National Institute of Standards and Technology (NIST) defines network segmentation as "splitting a network into sub-networks...by creating separate areas on the network which are protected...to reject unnecessary traffic. Network segmentation minimizes the harm of malware and other threats by isolating it to a limited part of the network."
Network segmentation is a powerful but underutilized security measure, and it is one of the cornerstones of a successful information security program. It directly addresses the reality of today's threat landscape--that you cannot prevent a cyber breach, but you can isolate one.
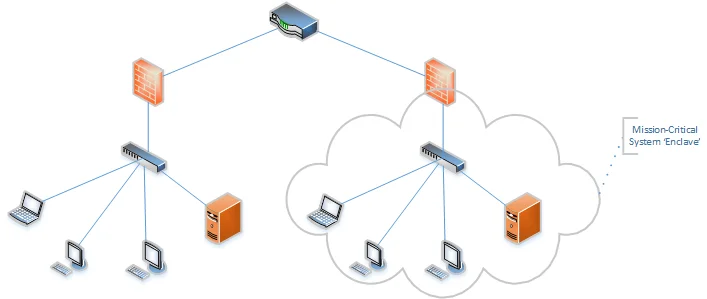
Figure 2 shows a simple representation of a segmented network, which, if properly implemented and managed, can greatly limit lateral movement. Organizations should carefully analyze the traffic required for the operation of any mission-critical systems. Only that traffic should be permitted and monitored by the appropriate network devices.
How to Implement Network Segmentation
Implementing network segmentation across an enterprise can take a lot of time and effort. The good news, however, is that in many cases your enterprise may have segmentation capabilities available within the network that simply haven't yet been deployed or configured. As with any cybersecurity implementation for new or existing systems, it's important to remember that you must determine what is feasible, what is reasonable, and what will not prevent the system from meeting its mission and business objectives.
In the remainder of this blog post we suggest some short-, medium-, and long-term actions that can help put an organization on a path toward segmentation and improve the enterprise's overall security posture. These actions can be roughly grouped into planning, preparation, and execution phases, though many of the activities can be done in parallel.
Planning Phase
To begin to address nonexistent or insufficient network segmentation, the organization must know (1) the network's current state, (2) available capabilities, and (3) what's required to achieve the desired state. It's essential to avoid analysis paralysis when planning and undertaking these enterprise improvement efforts. Also, seeking 100% knowledge or assurance (perfection), whether for current or future state, inhibits incremental improvements based on available (good enough) information. Many planning phase activities can be done concurrently.
Understand the Network's Current State:
1. Review (or develop if necessary) a validated functional network map.
2. Review or develop a validated inventory of assets that support mission-critical systems.
3. Review any existing security assessment findings to understand if they are isolated issues or indicators of broader enterprise issues.
a. If isolated, are there organizational network segmentation capabilities available that are not being leveraged? Why not?
b. If enterprise-wide, ensure there is no duplication of effort in remediation.
Identify Available Capabilities:
1. Identify the tools and infrastructure components utilized to control network traffic or flows (e.g., switches, routers, security devices) throughout the organization.
2. Determine which existing tools and capabilities within the organization can be configured or modified to better effect network segmentation.
Understand the Desired State Requirements:
1. Requirements can include short-, mid-, and long-term objectives that will improve the ability to monitor and manage network traffic and flows.
2. Review your cybersecurity governance and policies to identify derived, implied, and/or hidden requirements related to network segmentation. Topic areas that might seem unrelated at first (e.g., change control, incident response) could affect implementation or management of network segmentation.
Preparation Phase
Once armed with the above information, establish a project team, including key subject-matter experts and resources, that focuses on short-term deliverables while considering long-term strategy and impacts. Even if you have already started the processes and actions below, it's important to make sure they are aligned with the enterprise strategic and risk management goals.
Short-Term Actions:
1. Identify mission-critical systems at risk from a lack of network segmentation.
2. Utilize this information to identify potential mitigations. These mitigations may include endpoint agents, additional network or security devices, and/or adding or repurposing existing capabilities to create a secure enclave for each system.
3. Rank mitigation activities based on expected relative residual risk, ease of implementation, cost, and the organization's risk appetite.
4. Use this information to recommend to senior leadership courses of action and to request resources and authorization to implement them. Senior leadership support of significant changes to infrastructure or policy is imperative for success.
Medium-Term Actions:
1. Utilizing the information gathered above, including requirements, senior leadership goals and objectives, and the current state and capabilities, develop a strategic plan to improve network segmentation and mature related processes, ensuring security is designed in from the beginning.
2. Identify policy and process gaps that need to be addressed and initiate appropriate activities to correct them.
3. If not already done, develop an organizational reference architecture.
Long-Term Actions:
1. Develop a continuous improvement process to keep the reference architecture current and provide guidance in implementing new capabilities and services.
2. Determine metrics and measurements that quantify risk and threats to better measure success and cost-effectiveness of mitigation capabilities.
Execution Phase
In this phase, your organization begins to make network segmentation a reality using the groundwork laid in the prior phases. It may be necessary to adjust scheduling during execution due to conditions on the ground or to lessons learned. The notional timelines below can be adjusted based on the size and scope of the segmentation effort.
Short-Term Actions (<1 year):
- Establish mission-critical system enclave(s) in appropriate production infrastructures.
- Develop plans to migrate these systems into these newly-secured enclaves if required.
- Identify metrics and measures for quantifying mission-critical system operational performance in those enclaves to promote continuous improvement.
Medium-Term Actions (1-2 Years):
- Migrate the systems into the enclave(s) established above.
- Identify the organizational reference architecture that supports longer-term services delivery objectives and includes security requirements and capabilities.
- Develop a migration plan for that reference architecture.
Long-Term Actions (>2 Years):
- Execute long-term strategic migration to the reference architecture.
- Enable continuous improvement of services delivery via regular review and updates to requirements, policy, and reference architecture, utilizing performance metrics.
It's a Process
As with many cybersecurity concepts, network segmentation cannot be viewed as a singular event. It must instead be treated as a dynamic process conducted as mission-critical systems are introduced, updated, and decommissioned. The process may also be required in response to organizational mission changes, new or evolving threats, or changes to the organization's risk appetite. Having a coordinated strategy to govern the segmentation process ensures a formalized process and establishes the organizational "muscle memory" needed for consistency of application.
More By The Authors
Process and Technical Vulnerabilities: 6 Key Takeaways from a Chemical Plant Disaster
• By Daniel J. Kambic
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedGet updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed


