New Model Provides Blueprint for DevSecOps
• Article
May 26, 2022—The SEI this week released the DevSecOps Platform-Independent Model (PIM) that formalizes the practices of DevSecOps pipelines and organizes relevant guidance. The first-of-its-kind model gives software development enterprises a practical set of instructions for creating, maintaining, and evolving DevSecOps pipelines.
DevSecOps is a software engineering environment that promotes collaboration among development, security, and operations. This socio-technical system uses automation for flexible, rapid, frequent delivery of secure infrastructure and software to production. “DevSecOps encompasses all the best software engineering principles known today,” said Joe Yankel, an SEI senior engineer specializing in DevSecOps. “The result is more secure, more useable, and higher quality software systems.”
Software development organizations must tailor each DevSecOps pipeline to the people, processes, and technology needed to provide a product or service. These complex pipelines are especially hard for large projects and in heavily regulated, security-sensitive environments, such as banking, healthcare, and government.
The SEI has worked with multiple, large Department of Defense (DoD) software acquisition and development groups who faced challenges adopting DevSecOps methods. While policies, such as the Software Acquisition Pathway, encourage government programs to use DevSecOps and Agile methods, they do not say how.
Neither does the large but poorly defined body of DevSecOps literature. For example, the commonly depicted infinity diagram of DevSecOps obscures the many decisions in each phase. Similarly, the foundational IEEE 2675 Standard for DevOps cannot capture the complex interactions within a pipeline. Without a coherent, practical framework for DevSecOps, organizations often cannot fully integrate its practices into their policies, analyze alternatives, produce compatible DevSecOps projects and pipelines, or assure their security and function.
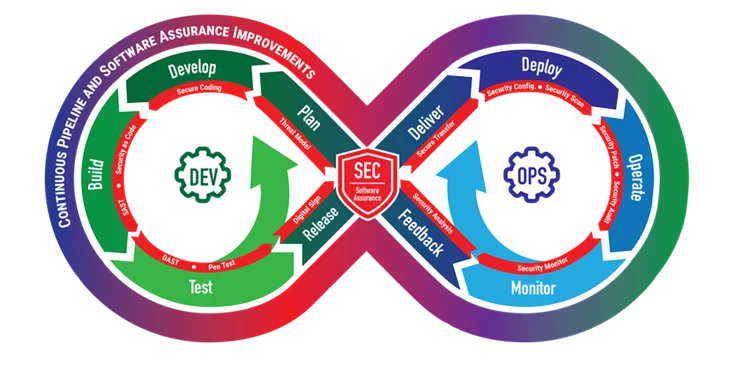
DevSecOps infinity diagram.
“Programs often focus on the product and don’t put enough effort into the pipeline that's building it,” said Tim Chick, technical manager of the SEI’s Systems team and PIM project lead. There is a guidance gap between the theoretical academic discussions of DevSecOps and the narrowly scoped DevSecOps tools, leaving organizations to create pipelines ad hoc. “That haphazard approach becomes a source of pain.” Without the right infrastructure, organizations fritter away resources fighting fire after fire. In the end, their DevSecOps implementations fail to yield their expected value.
The SEI’s new DevSecOps PIM is a general, reusable reference architecture for DevSecOps pipelines. Anyone can access an interactive version of the PIM on the SEI’s GitHub site and use the architecture as a systematic, consistent starting point for their own DevSecOps projects. The interactive PIM lets users walk the model and explore all the guidance associated with each phase of the DevSecOps lifecycle.
Any stakeholder in software development might find a use for DevSecOps PIM’s holistic, enterprise-wide view. Managers can discover required organizational roles, responsibilities, and processes. Best practices can inform executives’ policy making. Engineers can determine if they have the right tools. Acquisition officers can compare competing contractor bids against the model to see which approach fits best. “The PIM allows you to think through what you really need to meet your business goals and objectives,” said Chick, the PIM project lead.
Yankel, one of the PIM’s developers, agreed. He added that by helping organizations plan a DevSecOps infrastructure fit for purpose, the PIM is intended to keep organizations from accruing technical debt. “You know what you actually need to build versus buying something that doesn’t suit you,” he said.
Putting in the up-front work on a pipeline, with the PIM as a consistent source of truth, gives software development and acquisition organizations a host of abilities. They can use the DevSecOps PIM as a starting point for their own platform-specific DevSecOps pipelines for continuous integration and continuous delivery (CI/CD). Developers can specify requirements to system integrators, perform apples-to-apples analysis of alternative pipeline features, and apply DevSecOps methods to complex software products that do not follow established architectures. The model can provide a point of reference when examining existing pipelines for gaps.
The PIM also allows pipeline risk modeling and threat and attack surface analysis. The ability to create pipeline cyber assurance cases can help avoid events such as the SolarWinds attack, which exploited the complexity of the software supply chain. Each pipeline should be evaluated to minimize cybersecurity risks to both the pipeline and its products.
The PIM aims to help organizations fulfill the promise of DevSecOps: software that is more secure, less costly, and faster to produce.
The project sprang from conversations between Chick and his colleagues about two years ago. They wondered how a DevSecOps pipeline could be assured. “We realized that DevSecOps was so poorly defined, no one could perform the analysis needed to show you have a well-built, secure, predictable pipeline and environment. What material would be sufficient to enable this analysis? And what other questions would this be able to answer?”
A lot of other questions. As Chick and his colleagues gathered DevSecOps guidance around assurance, they realized they could combine model-based systems engineering (MBSE) and enterprise architecture to capture the social, technical, and process aspects of a DevSecOps system across its lifecycle—and beyond.
The PIM project’s enterprise approach accounts for all of an enterprise’s DevSecOps pipelines—not just building them but managing and interoperating them too. The PIM also includes a four-level DevSecOps maturity model covering the 10 capability areas of the DevSecOps lifecycle.
“The PIM is like a map,” said Chick. “The assessment aspects in the model will tell you where you are. Then you can look at the model and see what other activities you’re not doing or are weak at. You can plan where you want to go. The model helps you get there the most efficient and effective way.”
Tackling something as large and multifaceted as enterprise-scale software pipelines required expertise in nuts-and-bolts engineering, business processes, cybersecurity, maturity modeling, highly regulated environments, and more. The SEI brought together its experts from all these areas to produce the initial model and piloted it with government organizations. This week’s release marks the PIM’s public debut.
Just as development pipelines continuously evolve, so too will the PIM. The SEI invites feedback on the model through its GitHub site. Those interested in collaborating on the model can email info@sei.cmu.edu.
“It’s a living, breathing model that will go through iterations,” said Chick. “As we improve and learn more, it becomes a place to capture that knowledge base.”
Explore the model at the PIM interactive website. Learn more about the project and the SEI’s DevSecOps research on our website. Subscribe to the SEI Blog to be alerted to upcoming posts about the DevSecOps PIM by the SEI experts who created it. Also watch the SEI website for related podcasts.

