CERT/CC Releases VINCE Software Vulnerability Collaboration Platform
• Article
June 4, 2020—The SEI’s CERT Coordination Center (CERT/CC) this week rolled out a new, web-based platform for software vulnerability reporting and coordination called the Vulnerability Information and Coordination Environment (VINCE). The CERT/CC team is replacing its legacy system of more than 20 years to help scale communications and increase the level of direct collaboration between vulnerability reporters, coordinators, and software vendors.
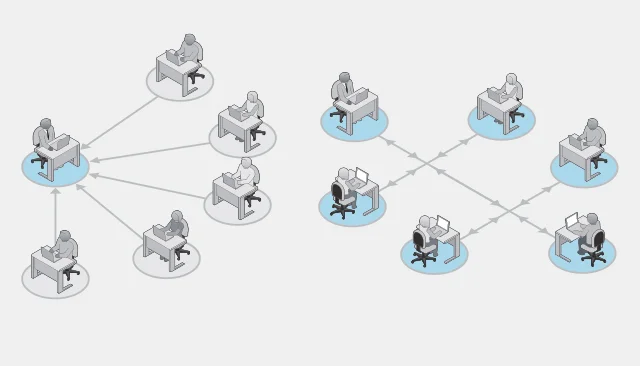
The change is more than an invisible, back-end transition. Until now, vulnerability coordination has relied on a hub-and-spoke model: CERT/CC sat in the center, receiving and passing on PGP-encrypted emails from those researching and reporting software vulnerabilities to the affected vendors and back. The new model underlying VINCE is more like a shared communication bus, where all stakeholders tap into a central, web-based platform to talk directly with each other.
Art Manion, vulnerability analysis technical manager in the CERT Division of the SEI, said that he doesn’t want CERT/CC to become a bottleneck to vulnerability coordination. “We are removing ourselves as the intermediary,” said Manion. “By using the bus model built into VINCE, we are trying to set an example that the protocol and the etiquette and the norm have shifted. We want all the vendors, researchers, and reporters in the same room. Everyone has a channel there and can work together.”
For each new vulnerability, CERT/CC creates a VINCE case discussion, which is a private message-board forum complete with the abilities to tag other participants, upload files, and send CERT/CC private messages. CERT/CC then invites reporters, researchers, and vendors related to the vulnerability to join the case discussion. To participate, stakeholders must have a VINCE account, and they can ask CERT/CC to add them to a case discussion. CERT/CC will continue to coordinate and moderate each case, but the stakeholders can work directly with each other, both before and after any public disclosure of the vulnerability.
The new platform debuted just weeks after the Forum of Incident Response and Security Teams (FIRST) released its Guidelines and Practices for Multi-Party Vulnerability Coordination and Disclosure. The FIRST guidelines aim to open the bilateral communications between security researchers and software vendors to all parties involved in a software vulnerability. The VINCE platform creates exactly the kind of common space needed to support multiparty communications around a vulnerability.
That was not the intent a year ago when Emily Sarneso, an application developer for the CERT Division and the lead developer of VINCE, was asked to update CERT/CC’s vulnerability reporting systems. “We were replacing each one piecemeal, and then we realized that the way we were doing it needed to be replaced, the whole hub-and-spoke idea,” she said. “We asked, ‘Why don’t we bring everybody together, so that we’re not just the middleman relaying all of this information to sometimes over 200 different organizations?’”
Sarneso said that when she and Manion presented this idea to vendors at this year’s RSA conference, they were met with trepidation. “Because we’ve done it one way for so long,” said Sarneso, “we’re really changing hearts and minds about a new vulnerability disclosure process.” They explained how being the go-between for reporters, researchers, and more than 2,300 software developers and vendors did not scale. Managing PGP keys for email encryption, updating vendor contact information, coordinating mass emails, and sorting out conflicting vendor disclosure policies was a time-consuming nightmare.
With VINCE, email gives way to a more secure web platform, and CERT/CC staff expect to spend more time directly coordinating complex cases, analyzing vulnerabilities, and studying standards such as CVE and CVSS. Stakeholders can update their own contact information, and the collaborative environment consolidates information to a shared space and fosters trust and goodwill.
In the spirit of more open communication, CERT/CC plans to make VINCE an open source download with an API so that organizations can pull its information into their own vulnerability tracking systems. “We feel like the biggest contribution from VINCE could be the creation of this shared language for different organizations to talk about vulnerabilities and vulnerability disclosure,” said Sarneso.
VINCE is now live on https://www.kb.cert.org/vince. Though the CERT/CC email will remain active, Manion and Sarneso encourage software vendors and cybersecurity researchers to create a VINCE account and not just coordinate on vulnerabilities, but truly collaborate.
Manion sees VINCE as part of the SEI’s mission, as a federally funded research and development center, to transition capability beyond its own walls. “Finding, fixing, patching, and defending against vulnerabilities—we’re trying to help others do it faster, better, and more easily,” said Manion. “It’s the same overall mission: reduce risk. It’s just a better, modern way to do it.”

