Malicious Insiders in the Workplace Series: What Positions Do Malicious Insiders Hold? (Part 2 of 4)
In the first part of this series, we analyzed the gender of malicious insiders as it relates to the categories of insider threat incidents. In this post, understanding the roles that insiders play within their victim organizations further contextualizes the insider threat landscape.
The following table displays the positions held by 675 malicious full- and part-time insiders separated by case type. The chart does not include incidents where the exact nature of the insider's position was unknown (97) nor incidents where the insider was a contractor (48). Percentages were calculated based on the number of incidents within each case type; for that reason, percentages by position (across each row) will not equal 100%.
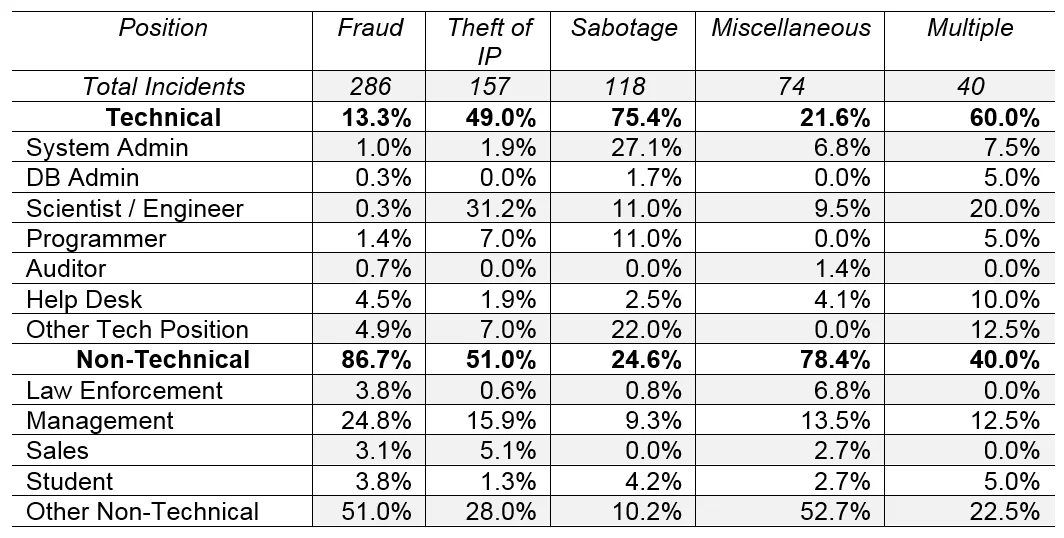
The statistics discussed in the remainder of this blog post focus only on incidents where the position of the insider is known.
Overall Insider Threat
The position types least held by known insiders were database administrator (5) and auditor (3). In general, many insiders held what are considered to be non-technical, non-management positions within their victim organizations, such as bank teller, physician, or office manager.
Fraud
Insiders holding non-technical positions accounted for 86.7% of fraud incidents. Malicious insiders held management positions in 24.8% of fraud incidents. Non-technical management staff, in most scenarios, had access to personally identifiable information (PII) or the victim organization's financial resources (i.e., money), the very targets in 59.9% of all fraud incidents.
Theft of IP
Theft of IP incidents were unique in that technical and non-technical staff were represented in almost equal proportions (i.e., a "50-50 split"). Scientists and engineers were most represented in Theft of IP, which in some cases were committed in response to disputes over intellectual property, as opposed to other case types. Within non-technical staff, management (15.9%) and other non-technical staff (16.57%) were the most represented within Theft of IP.
Sabotage
Technical staff committed 75.4% of sabotage incidents. System administrator was the most commonly held position (27.1%), accounting for 36.0% of sabotage incidents within the subsample of technical staff. Overall, this result suggests a greater representation of technical positions in IT sabotage incidents than in all other case types.
Additional Information
The following table displays the instances of insiders within unknown positions, or those holding contract positions, by case type. The percentages were calculated based on the number of incidents within each case type, accounting for 825 incidents in total.
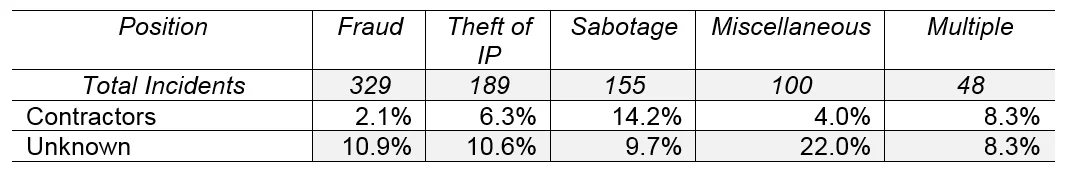
As shown, contractors were most represented in incidents of sabotage (14.2%) and insiders with unknown positions were most represented in miscellaneous incidents.
Findings and Further Reading
Despite using technical methods, a majority of the insider incidents within this subsample of the CERT Insider Threat Incident Corpus involved non-technical employees or contractors (456 or 63.07%). Based on the information in my previous blog post and the information shared here, we can tentatively begin to identify patterns regarding malicious insiders' gender and position in relation to case type.
In the next post in this series, I will analyze estimates of how much insiders are paid by the organizations where they commit their exploits.
For information about how technical controls can help prevent, detect, and respond to insider incidents, refer to the podcast Indicators and Controls for Mitigating Insider Threat.
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
