Welcome to the Insider Threat Blog
Hi, this is Dawn Cappelli, technical manager of the Insider Threat Center at CERT. Thanks for taking the time to visit our new insider threat blog. As many of you know, we've been doing insider threat research since 2001. Our mission is to raise awareness of the risks of insider threat and to help identify the factors influencing an insider's decision to act, the indicators and precursors of malicious acts, and the countermeasures that will improve the survivability and resiliency of the organization. Our transition strategy has always included research reports, conference presentations, workshops, journal articles, and podcasts, and we still plan to use those methods for communicating the results of our research. However, with the insider threat landscape changing so quickly, we believe a blog is an effective vehicle for addressing current issues in a timelier manner.
For this first blog entry, I'll give you a quick recap of our research into insider threat: what we've done, what we're doing now, and where we're headed.
We have been researching insider threat for almost 10 years and have collected a database of more than 400 insider cases that occurred in the U.S. across all critical infrastructure sectors and a database of more than 120 cases of national security espionage in the U.S. These continuously evolving databases provide the foundation for all of our research. Our case collection and analysis efforts have been funded by the U.S. Secret Service, the Department of Homeland Security, the Department of Defense, and Carnegie Mellon CyLab.
We recognize the importance of unintentional insider threats; however, our research to date has focused on intentional insider threats, which can be highly damaging to an organization. In addition, we believe that detection methods for intentional attacks could also be effective against unintentional data leakage. We define a malicious insider as a current or former employee, contractor, or other business partner who has or had authorized access to an organization's network, system, or data and intentionally exceeded or misused that access in a manner that negatively affected the confidentiality, integrity, or availability of the organization's information or information systems.
We categorize insider crimes as follows:
- IT sabotage: incidents in which insiders intentionally exceeded or misused an authorized level of access to networks, systems, or data with the intention of harming a specific individual, the organization, or the organization's data, systems, and/or daily business operations
- Fraud: incidents in which insiders intentionally exceeded or misused an authorized level of access to networks, systems, or data with the intention of stealing or modifying confidential or proprietary information from the organization for financial gain
- Theft of intellectual property: cases in which insiders intentionally exceeded or misused an authorized level of access to networks, systems, or data with the intention of stealing confidential or proprietary information from the organization with the intent to use it for a business advantage
The following graphic illustrates a breakdown of each type of insider crime in our database of threats to critical infrastructure sectors, as of August 2010.
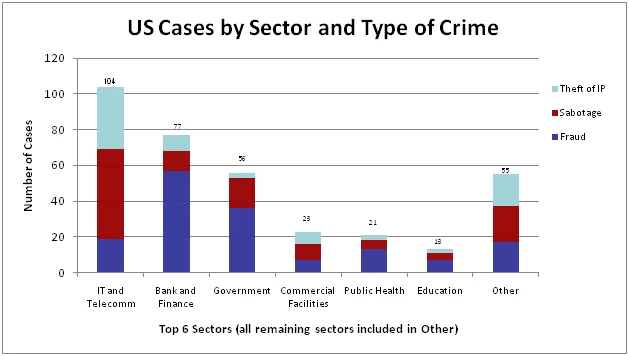
The CERT® Insider Threat Center performs academic research, develops solutions based on the results of that research, works with practitioners to apply and refine those solutions in real-life situations facing government and industry, then transitions those proven methods as broadly as possible. Recently, we created an insider threat lab to research, test, and apply new methods for preventing and detecting insider threats. One of our current focus areas is using the lab to develop insider threat controls using existing software technologies. For example, at the recent Government Forum of Incident Response and Security Teams (GFIRST) conference, we demonstrated how custom rule sets for log analysis software can detect unauthorized exfiltration of intellectual property.
See our Common Sense Guide to the Prevention and Detection of Insider Threat for a much more detailed analysis of the insider threat problem as well as some solutions.
In the coming weeks, we'll publish blog entries about our ongoing research, new analysis, and actionable research-based solutions that can be implemented to identify insiders in the enterprise. Our goal is to solve real problems facing industry and government, so please contact us using the feedback link on the bar to the right with questions and suggestions. Hope to hear from you soon.
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed