The Zero Trust Journey: 4 Phases of Implementation
PUBLISHED IN
Cybersecurity EngineeringOver the past several years, zero trust architecture has emerged as an important topic within the field of cybersecurity. Heightened federal requirements and pandemic-related challenges have accelerated the timeline for zero trust adoption within the federal sector. Private sector organizations are also looking to adopt zero trust to bring their technical infrastructure and processes in line with cybersecurity best practices. Real-world preparation for zero trust, however, has not caught up with existing cybersecurity frameworks and literature. NIST standards have defined the desired outcomes for zero trust transformation, but the implementation process is still relatively undefined. Zero trust cannot be simply implemented through off-the-shelf solutions since it requires a comprehensive shift towards proactive security and continuous monitoring. In this post, we outline the zero trust journey, discussing four phases that organizations should address as they develop and assess their roadmap and associated artifacts against a zero trust maturity model.
Overview of the Zero Trust Journey
As the nation’s first federally funded research and development center with a clear emphasis on cybersecurity, the SEI is uniquely positioned to bridge the gap between NIST standards and real-world implementation. As organizations move away from the perimeter security model, many are experiencing uncertainty in their search for a clear path towards adopting zero trust. Zero trust is an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources. The CERT Division at the Software Engineering Institute has outlined several steps that organizations can take to implement and maintain zero trust architecture, which uses zero trust principles to plan industrial and enterprise infrastructure and workflows. These steps collectively form the basis of the zero trust journey.
The zero trust journey is a cybersecurity game plan for public-sector and private-sector organizations alike, providing them with the technical guidance and reference materials necessary to ensure successful zero trust adoption. This groundbreaking approach leverages existing zero trust literature (such as NIST SP 800-207) and the CERT Division’s comprehensive security assessments (such as the SEI’s Security Engineering Risk Analysis and Mission Risk Diagnostic). Collectively, these resources will bolster an organization’s decision-making capabilities regarding zero trust.
For reference, we have provided a breakdown of the zero trust journey in the chart below.
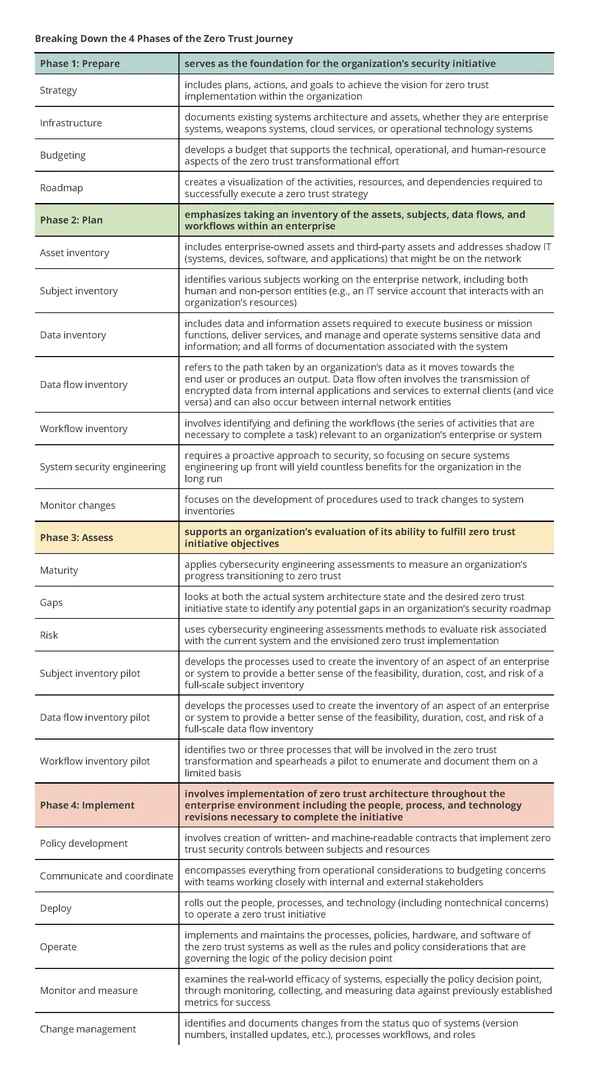
First Phase: Prepare
The Prepare phase encompasses a set of high-level tasks that will serve as the foundation for an organization’s security initiative. This phase is mission-oriented in nature and places significant emphasis on setting achievable goals and obtaining necessary buy-in from stakeholders.
The Prepare steps in the first phase include
- strategy— The importance of creating an effective and easily communicable zero trust strategy cannot be overstated. Strategy is essential for developing cohesion within an organization and reducing internal pushback regarding costs and logistical challenges. Strategy will include plans, actions, and goals to achieve the vision for zero trust implementation within the organization. It involves the development of a comprehensive organizational plan that identifies how zero trust investments achieve business and operational objectives.
- infrastructure—An organization must know what it has before it can consider the implementation of zero trust tenets. In its current-state architecture, the organization must document its existing systems architecture and assets, whether they are enterprise systems, weapons systems, or operational technology systems. Many organizations struggle to document existing systems architectures and assets, whether they exist in the cloud, on premises, or in a hybrid environment. In the past, some organizations have performed periodic asset assessments, but the necessary shift towards continuous monitoring requires a more dynamic approach to cyber threats. This effort will take time, so it is prudent to consider partitioning areas of the enterprise or system and dividing the zero trust effort into more manageable parts.
- budgeting—Turnkey, commercially available hardware, software, or cloud services that incorporate all zero trust tenets do not exist in the marketplace, so organizations cannot view transitioning to zero trust as just an acquisition effort. Organizations will need to develop a budget that supports the technical, operational, and human-resource aspects of the zero trust transformational effort. The budget should account for the staff, training, products, and services that will be implemented and maintained throughout the zero trust initiative, in addition to the monitoring needed to develop a dynamic zero trust policy decision point. Security initiatives require funding to ensure project success. The budgeting aspect is especially important because inadequate funding can stall mission progress, compromise system security, and create conflict and division within an organization.
- roadmap—The roadmap is a visualization of the activities, resources, and dependencies required to successfully execute a zero trust strategy. The roadmap will allow executives to evaluate the zero trust initiative to see if it supports the organization’s time frames (ideally both short and long term), costs, staffing needs, and business drivers. The roadmap can also be presented to organizational stakeholders to help secure their buy-in and solicit feedback on any gaps or inaccuracies in the envisioned strategy. The zero trust initiative will involve all aspects of the organization, so using the roadmap to initiate communication about possible impacts and tradeoffs in operational workflows is another important element of this phase.
Second Phase: Plan
The Plan phase emphasizes taking an inventory of the “assets, subjects, data flows, and workflows” within an enterprise. The Plan phase is crucial to the success of a zero trust initiative because “an enterprise cannot determine what new processes or systems need to be in place if there is no knowledge of the current state of operations.” The SEI’s experiences managing cybersecurity projects align with this sentiment. Organizations must perform several logistical tasks to facilitate their journey.
NIST SP 800-160, Volume 1 states that an organization must “identify stakeholder assets and protection needs and provide protection commensurate with the criticality of those assets and needs and the consequences of asset loss.” It also encourages organizations to “build trustworthy secure systems capable of protecting stakeholder assets.”
So, what is an asset? As identified in NIST SP 800-160, an asset may be tangible (e.g., hardware, firmware, computing platform, network device, or other technology component) or intangible (e.g., data information, software, trademark, copyright, patent, intellectual property, image, or reputation). In the Plan phase, an organization will work on inventorying its tangible assets, as well as its intangible assets: subject, data, data flow, and workflow. These inventories will be developed over a period of time as an organization often doesn't have the time to develop complete, exhaustive lists in this phase. Later on, the Assess phase recommends piloting these areas in a subset of the enterprise or system. These pilots enable an organization to focus on a smaller area and develop the processes used to perform the work.
The Plan steps in the second phase include
- asset inventory—Depending on the organization’s size, tangible asset inventories can be hard to develop because they include enterprise-owned assets, third-party assets, as well as addressing shadow IT (systems, devices, software, and applications) that might be on the network. An accurate asset inventory is critical to the zero trust journey as it allows organizations to identify security gaps, reduce unnecessary expenditures, and avoid potential system redundancies.
- subject inventory—Cybersecurity leaders must identify the various subjects working on their network, including both human and non-person entities (e.g., an IT service account that interacts with an organization’s resources). When taking the subject inventory, organizations should document highly critical entities, such as administrator and developer accounts. It is important to map out the key players in a network to fully understand the strengths and weaknesses of existing resources. In turn, the organization will gain the insight necessary to identify security vulnerabilities and compatibility issues before they can impact the zero trust initiative.
- data inventory—Organizations must catalog all digital information consumed and generated by systems selected for a zero trust initiative. Data and information assets include those required to execute business or mission functions, deliver services, and manage and operate systems; sensitive data and information (e.g., classified information, controlled unclassified information, proprietary data, trade secrets, privacy information, critical program information, and intellectual property); and all forms of documentation associated with the system. Data related to the policy decision point are especially important to enumerate during the zero trust initiative. For federal organizations, this step is heavily influenced by the Cloud Smart Strategy, Data Center Optimization Initiative, and the Federal Data Strategy. An organization might already have a data inventory available for reference, but if it doesn’t, it should work toward recording how it collects, stores, and accesses data, both on-site and in the cloud.
- data flow inventory—In a zero trust network, data flow typically refers to the path taken by an organization’s data as it moves toward the end user. Data flow often involves the transmission of encrypted data from internal applications and services to external clients (and vice versa) and can also occur between internal network entities or between intelligence feeds and the application that provides the zero trust architecture policy decision point. An example of data flow would be the transfer of personably identifiable information (PII) data from a records database to an end user. As a rule of thumb, a data flow inventory should document the flow of data between subjects, assets, and resources selected for a zero trust initiative. The data flow inventory tends to work synergistically with the workflow inventory, since data flow is often related to business processes and the mission of the organization or agency.
- workflow inventory—Organizations interested in zero trust adoption must strive to document the working business and mission processes for systems selected for a zero trust initiative. By identifying an organization’s unique workflows, the implementation team will better understand the baseline or normal operations and related technical infrastructure needs. An example workflow could include the steps necessary for updating a database on the network (checking software versions, installing patches, etc.). Workflows and business processes can also be ranked and categorized based on organizational importance, impact on the user or subject, and the status quo of resources involved in the workflow. The categorization process can be further refined by using reference materials, such as the NIST Risk Management Framework (SP 800-37).
During the Plan phase, organizations must also decide how to apply zero trust tenets to the enterprise or system. An excellent starting point, based on NIST guidance, focuses on system security engineering.
- system security engineering— Zero trust requires a proactive approach to security, so focusing on secure systems engineering up front will yield countless benefits for the organization in the long run. When planning a zero trust transformation, it is important to incorporate “purposeful security design or configuration through a process that captures and refines security requirements and ensures their integration.” Planning for secure systems engineering is an all-hands activity that should involve both technical and nontechnical stakeholders. Organizations should reference NIST SP 800-160 Vol. 1 and NIST SP 800-160 Vol. 2 and related engineering standards when looking to adopt industry best practices for building secure systems.
The last step of the Plan phase ensures that organizations capture changes that occur either in the different inventories or decisions made during the system security engineering process.
- monitor changes—Zero trust is an organizational culture that must be maintained long term; it does not stop after implementation. As a means of strengthening organizational security culture, the monitor changes step focuses on the development of procedures used to keep track of changes to system inventories (assets, subjects, data flows, and workflows) and operations selected for a zero trust initiative. Inventories require significant time and effort to develop from scratch, so organizations should actively keep them up to date to avoid operational and logistical headaches. Monitoring changes will also allow the organization to better understand ongoing operations, identify anomalous activity, and highlight opportunities for improvement and growth.
Third Phase: Assess
Activities in the Assess phase support an organization’s evaluation of its ability to fulfill zero trust initiative objectives. This phase involves assessments focused on identifying maturity, gaps, and potential risks. It also involves pilot inventories to document the subjects, data flows, and workflows within the enterprise. The Assess phase assumes that the organization already has processes in place and is conducting routine asset and data inventories.
The Access steps in the third phase include
- maturity—Zero trust transformation is an endeavor that requires diligent monitoring of progress. This task applies cybersecurity engineering assessments to measure an organization’s progress transitioning to zero trust. To set benchmarks for progress, organizations can utilize emerging frameworks, such as the preliminary CISA Zero Trust Maturity Model, which covers a broad range of IT domains such as identity, devices, network and environment, application workload, and data. The CISA Zero Trust Maturity Model categorizes maturity as Traditional, Advanced, or Optimal for each IT domain. An organization’s maturity level can be measured using the cybersecurity engineering assessments described in the risk section below. These assessments will synergistically paint a picture of how far the organization has come and how far it still needs to go.
- gaps—When working toward a zero trust initiative, it is important to look at both the actual system architecture state and the desired zero trust initiative state to identify any potential gaps in an organization’s security roadmap. Performing cybersecurity engineering assessments up front and throughout the transformation lifecycle will help the organization identify gaps between its current position and desired end state. If the organization identifies gaps, it should perform risk analysis of these gaps to determine their impact on the zero trust roadmap and prioritize possible mitigations to address the gaps.
- risk—As mentioned in the maturity section, organizations can use cybersecurity engineering assessments (SEI Mission Risk Diagnostic [MRD] and Security Engineering and Risk Analysis [SERA]) to evaluate risk. These assessments will give an organization a better understanding of where its zero trust architecture implementation currently stands in comparison to desired maturity levels. MRD assesses an organization’s overall mission risk through comprehensive questionnaires, risk factor evaluations, and mission assurance profiling. On a more technical level, SERA involves the analysis of security risks throughout the organization’s “software-reliant systems and systems of systems.” It typically requires a full review of the system interfaces, enterprise architecture, threat profile, and mission thread. In a similar vein, CSER compares an organization’s current security posture against established cybersecurity engineering best practices to see where the organization stands technically. Collectively, these assessments provide significant intelligence regarding the costs associated with achieving a particular maturity level. In turn, the leadership team can make prudent, well-informed decisions regarding the direction of the zero trust journey.
- subject inventory pilot—Prior to executing the zero trust initiative on an enterprise-wide scale, project leaders should conduct a small scale subject inventory that tests the feasibility, duration, cost, and risk of a full-scale subject inventory. Conducting a subject pilot inventory is essential for scaling the initiative responsibly. The transformation team should begin planning and designing the inventory pilot study by defining the problem on hand (identifying the subjects that will fall within the scope of the zero trust initiative) and determining a method for measuring success of the pilot (e.g., level of accuracy in identifying subjects). The transformation team should carefully identify several low-value subjects that can be isolated from the remainder of the enterprise and used as part of the pilot. After deciding on the location and scope of the pilot, the inventory can be executed, documented, and evaluated for success against the predefined baseline metrics.
- data flow inventory pilot—This pilot entails a small-scale data flow inventory that tests the feasibility, duration, cost, and risk of a full-scale data flow inventory. The data flow inventory pilot will serve as a precursor to the full inventory, allowing the organization to fine tune its approach toward the process. The pilot should select two or three data assets and document how they are used within the enterprise. This will involve looking at the enterprise’s architecture to see where the data goes, as well as what interacts with the data. Any constraints or governance associated with the data should be identified. This pilot will also provide organizations with the experience necessary to look at other data assets within their zero trust roadmap as they develop this inventory.
- workflow inventory pilot —For similar reasoning as for the other pilots, the organization should complete a workflow inventory pilot. The transformation team can identify two or three processes that will be involved in the zero trust transformation and spearhead a pilot to enumerate and document them on a limited basis. As discussed in the previous inventories, procedural changes can be implemented after completion to optimize the full-scale workflow inventory.
Fourth Phase: Implement
The final step of the zero trust journey involves implementation of zero trust architecture throughout the enterprise environment. During this phase, the transformation team will perform the people, process, and technology revisions necessary to complete the initiative. This phase is heavily focused on policy development, communication, deployment, operation, monitoring, and change management activities, including
- policy development—This process involves the creation of written- and machine-readable contracts that implement zero trust security controls between subjects and resources. Zero trust is a policy-driven security model that requires written documentation and digital parameterization for successful implementation. Written policies are essential for dictating proper functionality and procedures and integrating the human element into a zero trust architecture. On the other hand, digitally inputted policies are essential for dictating a system’s operating parameters. Collectively, these policies will ensure proper functionality of the policy decision point and engine.
- communicate and coordinate—Essential aspects of a successful zero trust transformation include maintaining clear lines of communication and coordination. Throughout the implementation process, transformation teams should work closely with internal and external stakeholders to discuss their needs. These conversations should encompass everything from operational considerations to budgeting concerns. Furthermore, the transformation team should be receptive to the needs, wants, questions, and concerns raised by stakeholders. The organization should use modern project management processes to ensure clear and effective communication throughout the initiative lifecycle.
- deploy—At this point, the transformation team is focused on rolling out the people, processes, and technology required to operate a zero trust initiative. This can be a particularly challenging and stressful time for an organization, but the previous steps of the zero trust journey will have laid down a solid foundation for successful deployment. Deployment is heavily focused on modifying or replacing existing hardware and software to work with zero trust, but it also involves nontechnical concerns, such as adjusting business processes and training personnel. Deployment should occur slowly and methodically based on business priorities, risks, and asset valuation.
- operate—Once an aspect of zero trust architecture has been implemented, impacted personnel should be fully briefed on the functionality and architecture of the zero trust systems. Furthermore, they should be made aware of the rules and policy considerations that are governing the logic of the policy decision point and engine. Clear communication and training are essential to maintaining successful security operations in the long term. Organizations should focus on automation to streamline security operations. Automation can scale up the security capabilities and help ensure constant protection. On the other hand, the organization’s cybersecurity personnel should be fully prepared to intervene when a security incident is detected.
- monitor and measure—As time goes by, the organization will shift its priorities towards
watching and logging zero trust infrastructure operations and evaluating its quality and effectiveness toward meeting intended objectives. Put more simply, the organization should be looking at the real-world efficacy of its systems, especially regarding the policy decision point. This activity is accomplished through monitoring, collecting, and measuring data against the organization’s previously established metrics for success. As a result, the organization will gain a better understanding of the strengths and weaknesses of its zero trust systems. From there, the organization can make the necessary changes to optimize the functionality of its policy decision point and zero trust systems. - change management—An organization needs to focus on identifying changes from the status quo of systems (version numbers, installed updates, etc.), processes workflows, and roles; documenting the reason for the changes. Automation should be considered for this area to evolve to support providing dynamic inputs into the organization’s policy decision point capability for inclusion in risk considerations.
A Successful Zero Trust Security Transformation
By implementing the four phases outlined in this post, organizations can execute a successful zero trust security transformation and bring hardware, software, processes, and personnel into alignment with emerging regulations and standards. This transformation will not occur overnight. Organizations will have to continuously consider and address zero trust tenets to ensure the long-term security of their systems.
Additional Resources
View the webcast Zero Trust Journey by Tim Morrow and Geoffrey Todd Sanders.
View the podcast Zero Trust Adoption: Benefits, Applications, Resources by my colleague Geoffrey Todd Sanders.
More By The Authors
More In Cybersecurity Engineering
PUBLISHED IN
Cybersecurity EngineeringGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Cybersecurity Engineering
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed


