CERT
Blog Posts
Process and Technical Vulnerabilities: 6 Key Takeaways from a Chemical Plant Disaster

Weak processes can be as risky as technical vulnerabilities. This post describes how both of them worsened a cyber attack on a chemical plant.
• By Daniel J. Kambic
In Enterprise Risk and Resilience Management

Designing Great Challenges for Cybersecurity Competitions
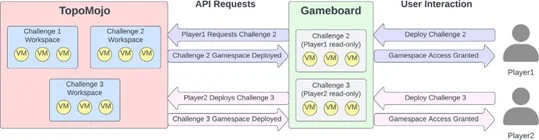
This blog post highlights the SEI’s experience developing cybersecurity challenges for the President’s Cup Cybersecurity Competition and general-purpose guidelines and best practices for developing effective challenges.
• By Jarrett Booz, Josh Hammerstein, Matt Kaar
In Cyber Workforce Development


Using Machine Learning to Increase the Fidelity of Non-Player Characters in Training Simulations
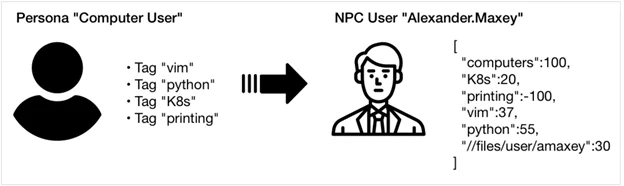
Use of machine-learning (ML) modeling and a suite of software tools to create decision-making preferences that make non-player characters (NPCs) more realistic in simulations.
• By Dustin D. Updyke, Thomas G. Podnar, Geoffrey B. Dobson, John Yarger
In Cyber Workforce Development


DNS Over HTTPS: 3 Strategies for Enterprise Security Monitoring

DNS over HTTPS (DoH) can impair enterprise network visibility and security by bypassing traditional DNS monitoring and protections. In this post, I'll provide enterprise defenders three strategies for security monitoring …
• By Sean Hutchison
In Cybersecurity Engineering

Generating Realistic Non-Player Characters for Training Cyberteams
This SEI Blog post describes efforts underway to improve the realism of non-player characters (NPCs) in training exercises with new software called ANIMATOR.
• By Dustin D. Updyke, Tyler Brooks
In Cyber Workforce Development


Balancing Cyber Confidence and Privacy Concerns
Learn about the privacy protocols that make it hard to protect enterprise networks, and their impact on network traffic monitoring in this SEI Blog post.
• By Bill Reed, Dustin D. Updyke
In Enterprise Risk and Resilience Management


Six Free Tools for Creating a Cyber Simulator
It can be hard for developers of cybersecurity training to create realistic simulations and training exercises when trainees are operating in closed (often classified) environments with no ability to connect …
• By Joseph Mayes
In Cyber Workforce Development

Evaluating Threat-Modeling Methods for Cyber-Physical Systems
Addressing cybersecurity for a complex system, especially for a cyber-physical system of systems (CPSoS), requires a strategic approach during the entire lifecycle of the system....
• By Nataliya Shevchenko
In Enterprise Risk and Resilience Management

Improving Assessments for Cybersecurity Training
The CERT Cyber Workforce Development Directorate conducts training in cyber operations for the DoD and other government customers as part of its commitment to strengthen the nation's cybersecurity workforce....
• By April Galyardt
In Artificial Intelligence Engineering

Threat Modeling: 12 Available Methods
Almost all software systems today face a variety of threats, and the number of threats grows as technology changes....
• By Nataliya Shevchenko
In Enterprise Risk and Resilience Management
