Malicious Insiders in the Workplace Series: How Does an Insider's Gender Relate to the Type of Incident? (Part 1 of 4)
Much attention has been paid to understanding the impacts of an insider threat incident. In examining recorded cases, trends begin to emerge over time just as with any other data set. However, despite these malicious insiders using technical means to cause harm, there is still a human component that should be considered. Who, collectively, are these malicious insiders that caused harm? What do we know about them? This blog post is the first of a four-part series about understanding insider threats.
Aggregated contextual information about insiders has been collected in CERT's Insider Threat Incident Corpus. By looking at trends that exist within a sample of 820 recorded insider incidents, we can begin to establish what is known and unknown about those incidents. With this information, you can consider to what extent these circumstances and potential threats exist within your organization.
First, to get a sense of what is known and unknown about the threat landscape, we can look at a simple demographic feature: gender.
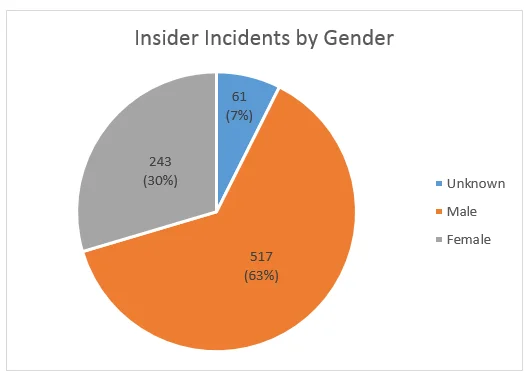
As shown in the pie chart above, nearly two-thirds of all the incidents in the CERT insider corpus were committed by males. Incidents where the insider is known, but no specific named individual is available, comprise the unknown gender category. Gender, with regards to this sample, is a simple proxy for how complete our knowledge of the insider is. In other words, if we do not know their gender, we may not know much about them in general.
However, taking gender into account when surveying the insider threat landscape by incident type provides more analytical value than when considering gender alone.
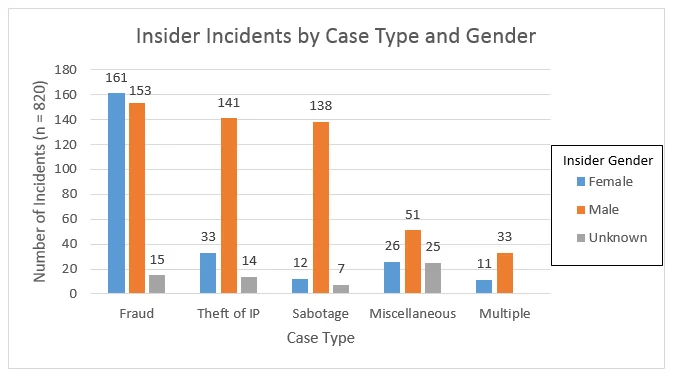
Since most of the malicious insiders are male, one would expect that would hold true for the various case types. Indeed, male malicious insiders are 4 times more likely than female malicious insiders to commit theft of intellectual property and 11.5 times more likely to commit IT sabotage. However, the graph clearly shows that female malicious insiders are most associated with incidents of fraud.
The second entry of this blog series will take into consideration the positions held by malicious insiders and how they relate to the type of insider attack committed. For an overview of the main categories of insider threat incidents, refer to Analyzing Insider Threat Data in the MERIT Database.
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
