Information Resilience in Today's High Risk Information Economy
Earlier this month, the U.S. Postal Service reported that hackers broke into their computer system and stole data records associated with 2.9 million customers and 750,000 employees and retirees, according to reports on the breach. In the JP Morgan Chase cyber breach earlier this year, it was reported that hackers stole the personal data of 76 million households as well as information from approximately 8 million small businesses. This breach and other recent thefts of data from Adobe (152 million records), EBay (145 million records), and The Home Depot (56 million records) highlight a fundamental shift in the economic and operational environment, with data at the heart of today's information economy. In this new economy, it is vital for organizations to evolve the manner in which they manage and secure information. Ninety percent of the data that is processed, stored, disseminated, and consumed in the world today was created in the past two years. Organizations are increasingly creating, collecting, and analyzing data on everything (as exemplified in the growth of big data analytics). While this trend produces great benefits to businesses, it introduces new security, safety, and privacy challenges in protecting the data and controlling its appropriate use. In this blog post, I will discuss the challenges that organizations face in this new economy, define the concept of information resilience, and explore the body of knowledge associated with the CERT Resilience Management Model (CERT-RMM) as a means for helping organizations protect and sustain vital information.
A New Information Economy
The information economy is transforming every public and private sector, including the way we deliver healthcare and educational services, fight wars and provide national security, design and operate critical infrastructure, build cities and communities, and manufacture goods. The following are some characteristics of the current environment that indicate we now operate in an information economy:
Intangible goods (e.g., information, ideas, and intellectual assets) continue to increase in absolute value and relative volume. This trend is apparent from the fact that the market capitalization of the largest entities in the world is increasingly based on the value of their information assets (e.g., customer records patient information, intellectual property, trade secrets, consumer purchasing and browsing data, new product specifications), and not solely their physical assets (e.g., land, buildings, equipment, and raw material). For businesses, information has moved from a supporting role to a leading role in determining mission success to the point that information is now among the highest valued assets, products, and services. It is almost as if the bits that make up the information are more important than the atoms that make up the infrastructure and the environment that the information resides in.
Physical and cyber (i.e., virtual) worlds are increasingly intertwining, and their boundaries have blurred. This change is reflected in the fact that virtual goods and environments are replacing their physical counterparts (e.g., virtual grocery store coupons; virtual business parks; virtual ballot box; virtual offices; virtual jobs; virtual stock markets; virtual water coolers such as cloud-based collaboration tools, online chat groups, and other types of social media). Even bank robberies are virtual, and can be instigated from a different continent. People (the initial users of the Internet), businesses (the next generation of Internet users in the form of eCommerce), and things (in the sense of the Internet of Things) are converging into a ubiquitous evolutionary information marketplace.
Content (i.e., information) developers and owners are the kings, not the equipment manufacturers (on whose systems the content is viewed) or the communication service providers (through which the content is delivered).
Immediacy is valued more than thoughtfulness, correctness, and the absence of defects. Technological advancements are developed and put into practice at a speed that makes them inherently unpredictable and often disruptive. Every innovation comes with flaws that someone will eventually exploit for personal gain. This technological whirlwind has thus spawned an ever expanding and dynamic operational risk environment.
Evolving in the Risk Environment
One of the primary success factors in the information economy is the manner in which organizations protect their information assets while operating in a volatile risk environment. Traditional IT security has been the underpinning of e-commerce. Without it, businesses and consumers would not have had the trust and confidence to use the Internet. For organizations to survive and thrive in today's information economy, however, they must manage risks to information assets in terms of all forms of technology that create, process, store, disseminate, and consume information, They include conventional information technologies, the ever-changing operational technology (OT), such as industrial control systems, physical access control mechanisms, etc., as well as the rapidly evolving and expanding Internet of Things (IoT).
Traditional IT security has focused on the management of security risks within an organization's enterprise IT environment, often performed by an IT security organization. Meanwhile, separate teams manage risk associated with other forms of technology, such as operational technologies (OT) that monitor and control physical devices and processes (e.g., industrial control systems) and where non-IT work processes are involved.
With the blurring of boundaries in the information economy, organizations must consider risk assessment and management across all forms of technology and assets. A more consistent and unified approach to information risk management will result in increased confidence and greater assurance that realized risk will not affect an organization's ability to achieve its business mission.
Moreover, risks associated with various forms of technology are only one dimension of operational risk in today's information economy. Proper protection and sustainment of information assets must go beyond technology-focused risk management activities. Traditional concepts of IT security (and the closely associated concepts of information security, information assurance, and cybersecurity) must evolve beyond their current technology scopes and be augmented by techniques and concepts from such domains as physical security (of tangible assets), safety (of people assets), and privacy (of personal information).
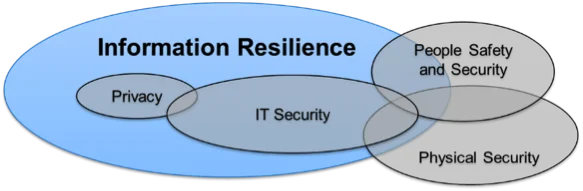
Information Resilience
The next step for organizations to consider is information resilience, which we define as the ability to protect and sustain critical information assets throughout their entire lifecycle (whether they are being created, processed, stored, disseminated, or destroyed) regardless of where such assets physically reside at any point in their lifecycle. In addition to preventing and defending against disruptions to technologies, information resilience emphasizes response and continuity during times of stress across technologies, people, and facilities.
Information resilience is concerned with information assets in two separate but interrelated dimensions:
- lifecycle dimension - the stages of information creation, processing, storage, dissemination, and destruction (where some of the stages may take place in different order and/or in parallel)
- containment dimension - the containment of information in technology, people, and/or facility assets at any point in its lifecycle
Information resilience addresses the entire operational risk landscape for information assets that are critical for enabling the organization's mission success in the information economy. Protection and sustainment considerations, therefore, apply to information assets in every aspect and intersection of these dimensions.
Given the proliferation of data typical in the information economy, information assets must be prioritized. For example, critical information assets may be those that are used in mission-critical services, information entrusted to the business by others, intellectual property, or information essential to operation of the business, such as vital records and contracts. Identifying critical assets makes all other information resilience practices feasible.
Profiles can be created for critical information assets to specify their confidentiality, availability, integrity, custody, privacy, sensitivity, and acceptable use requirements (collectively, resilience requirements). They can also be used to characterize the individuals (e.g., employees, suppliers, customers, contractors, regulators) who have access to them, containers (e.g., people, devices, facilities) on which the information resides, the units (e.g., systems, applications, brains) in which it is processed, and the environment (e.g., electronic networks, transportation infrastructure) over which it may be transferred.
Satisfying the resilience requirements of critical information assets requires continuous risk management (i.e., identifying risks whenever and wherever information assets are created, stored, transported, and processed, assigning dispositions to risks, and mitigating or otherwise handling risks). Administrative, technical, and physical protection controls must be applied as appropriate to meet resilience requirements. Configuration control should be used to establish baselines and point-in-time captures of information assets.
Methods for Managing Information Resilience
Approaches for assessing, improving, and managing information resilience could be ad hoc or based on some structured methodology. Information resilience requires involvement and contributions from such domains as IT, OT, IoT, physical security, safety, and privacy. Therefore, an ad hoc approach will likely not produce the desired and sustainable results. Efforts to assess, improve, and manage information resilience should be based on proven and structured approaches that provide repeatable, predictable, high-quality outcomes. Use of such comprehensive and flexible frameworks as the CERT Resilience Management Model (CERT-RMM) and the associated body of knowledge can help in achieving a sustainable capability.
There are many effective and appropriate ways for an organization to use CERT-RMM to guide, inform, or otherwise support improvements to its information resilience management activities. For those familiar with the concept of process improvement, CERT-RMM can be used as the body of knowledge that supports model-based process improvement activities for information resilience management principles and practices. Alternatively, a targeted improvement roadmap (which is a term used to designate a specific collection of CERT-RMM domains that a collectively address a specific objective), has been defined to assist organizations in planning and guiding their journey towards enterprise-wide information resilience.
Benefits of using such structured frameworks include
- enabling native incorporation of operational risk management principles and practices into the organization's cultural norm or DNA ( i.e., it is integrated into the normal course of rhythm of the business)
- ensuring that risk-based activities align with organizational risk tolerances and appetite
- serving as the starting point for socializing important harmonization and convergence principles across IT, OT, IoT, physical security, privacy, etc.
- facilitating collaboration between activities that have similar operational risk management objectives
- maintaining a business mission focus
- improving confidence in how an organization responds in times of operational stress
- enabling measurements of effectiveness
- enabling institutionalization and culture change
- guiding improvement in areas where an organization's capability does not equal its desired state
Cost-Benefit Issues
Several issues should be considered if an organization wants to maximize the value of adopting an information resilience approach. First, the need to protect information assets must be continually balanced with the need to run the business. Second, an objective of total prevention of disruptive events that negatively affect information assets (e.g., cyber-attacks) is not practical. And third, treating all risks and all information assets equally is not cost effective. The most important information assets must be identified and the protection and sustainment measures related to them prioritized.
Looking Ahead
Today's information economy has reshaped the organizations, industries, and communities that we are part of, creating new technological capabilities and business opportunities while blurring digital and physical worlds. At the same time, however, it has created new security challenges that feed an ever more dynamic and expanding risk environment that is simply beyond the scope of a traditional IT security function. A more consistent and unified approach to information risk management will result in increased confidence and greater assurance that realized risk will not affect an organization's ability to achieve its business mission.
Information resilience is such an approach. It is a more overarching, and manageable, concept that promises to be a key tool in our tool box of techniques for protecting and sustaining organizations' critical information assets and associated dependent business products, services, and missions. It is a critical dimension of operational resilience as defined by CERT-RMM, which, in addition to information asset resilience, addresses the resilience of technology, people, and facility assets.
Additional Resources
For more information about CERT's Resilience Management Model (CERT-RMM)
For more information about information economy and related transformations
- https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/206944/13-901-information-economy-strategy.pdf
- https://www.gartner.com/en/products/special-reports
- https://www.forbes.com/sites/gartnergroup/2014/05/07/digital-business-is-everyones-business/
- https://fortune.com/2014/02/27/box-ceo-how-will-your-company-compete-in-the-information-economy/
- http://ide.mit.edu/
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedGet updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
