Declaring War on Cyber Terrorism...or Something Like That
PUBLISHED IN
CERT/CC VulnerabilitiesBuzzwords are a mainstay in our field, and "cyberterrorism" currently is one of the hottest. We understand that terrorism is an idea, a tactic for actor groups to execute their own operations. Terrorists are known to operate in the physical world, mostly by spreading fear with traditional and non-traditional weaponry. As information security analysts, we also see products where "terrorists" are ranked in terms of sophistication, just like any other cyber threat actor group. But how does the definition of "terrorism" change when adding the complexities of the Internet? What does the term "cyber terrorism" actually mean?
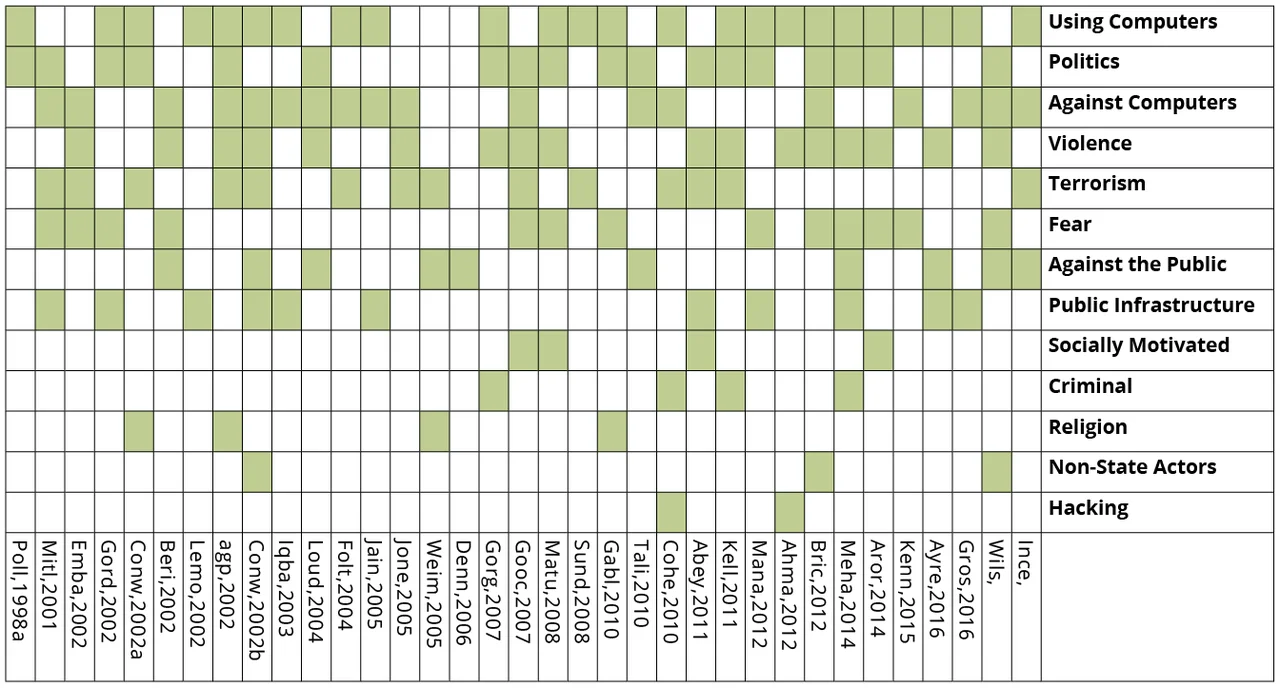
We identified thirty-seven (37) unique definitions of "cyber terrorism" drawn from academic and international-relations journals, the web, and conference presentations. These definitions date back as far as 1998, with the most recent being published in 2016. We excluded any circular definitions based on the findings in our set. We broke down these definitions into their main components in order to analyze and compare definitions appropriately. The definitions, as a whole, broke into the following thirteen (13) categories, although no single definition included all of them at once:
- Against Computers: Computers are a necessary target of the action.
- Criminals: Actions performed are criminal acts, according to the relevant applicable law.
- Fear: The action is intended to incite fear in the victims.
- Hacking: The attempt to gain unauthorized access into a targeted network.
- Religion: Religious tenants are a motivator to perform actions.
- Socially Motivated: Social constructs motivate to perform action on objectives.
- Non-State Actors: Individuals or groups not formally allied to a recognized country or countries.
- Politics: The political atmosphere and other occurances within a country or countries motivate action.
- Public Infrastructure: Government-owned infrastructure is a target of the action.
- Against the public: Actions performed against a group of people, many of which are bystanders.
- Terrorism: Violence perputrated by individuals to intimidate others into action.
- Using Computers: Computers are used during actions on objectives.
- Violence: The use of force to hurt or damage a target.
After binning each part of the definitions into these categories, we found that there is no consensus definition for "cyber terrorism." Our analysis of each definition is found in Figure 1. A factor that might explain the diversity of opinions could be the lack of a singular, agreed upon definition for "terrorism" on the international stage, even before adding the "cyber" adjective. So, what does this mean for us?
In the information security field, vendors, analysts, and researchers tend to slap the term "cyber" onto any actions involving an internet connection. While this may be appropriate in some cases, terrorism does not seem to translate well into bytes and packets. Perhaps this is due to the physical, visceral nature that terrorists require to be successful, or perhaps it is due to the lack of a true use-case of a terrorist group successfully detonating a computer. We should remain mindful as a community not to perpetuate fear, uncertainty, or doubt by using terms and varying adjectives without a common understanding.
More By The Authors
More In CERT/CC Vulnerabilities
PUBLISHED IN
CERT/CC VulnerabilitiesGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In CERT/CC Vulnerabilities
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed



