Archive: 2022
UEFI – Terra Firma for Attackers
This blog post focuses on how the vulnerabilities in firmware popularized by the Uniform Extensible Firmware Interface create a lucrative target for high-profile attackers.
Read More•By Vijay S. Sarvepalli
In CERT/CC Vulnerabilities

Networking at the Tactical and Humanitarian Edge
This blog post details networking challenges in edge environments that stem from uncertainty and solutions to overcome them.
Read More•By Marc Novakouski, Jacob Ratzlaff
In Edge Computing


Taking Up the Challenge of Open Source Software Security in the DoD
This post describes a workshop hosted by the SEI to start a conversation to elevate the trustworthiness of free and open source software, particularly in DoD settings.
Read More•By Scott Hissam
In Secure Development

10 Years of Research in Technical Debt and an Agenda for the Future
This post reviews the evolution of the field of technical debt and identifies open research questions that will drive future developments.
Read More•By Robert Nord, Ipek Ozkaya
In Technical Debt


Saying Why: Persona-Based Metrics With User Stories
This post discusses how to reframe metrics as user stories to improve their relevance and utility.
Read More•By Will Hayes, Patrick R. Place
In Agile


The Latest Work from the SEI: Digital Engineering, AI, and Deepfakes
This post highlights the latest work from the SEI in the areas of deepfakes, AI engineering, and digital engineering.
Read More•By Douglas Schmidt (Vanderbilt University)
In Software Engineering Research and Development

How to Grow an AI-Ready DoD Workforce
This SEI Blog post discusses the unique challenges of AI engineering for defense and national security, how to build an AI-ready workforce, and how the SEI is supporting DoD workforce …
Read More•By Robert W. Beveridge
In Artificial Intelligence Engineering

Using Alternate Data Streams in the Collection and Exfiltration of Data
In this blog post, we describe how attackers obscure their activity via alternate data streams (ADSs) and how to defend against malware attacks that employ ADSs.
Read More•By Dustin D. Updyke, Molly Jaconski
In Cybersecurity Engineering


Vultron: A Protocol for Coordinated Vulnerability Disclosure
This post introduces Vultron, a protocol for multi-party coordinated vulnerability disclosure (MPCVD).
Read More•By Allen D. Householder
In CERT/CC Vulnerabilities

The Drive Toward Stability
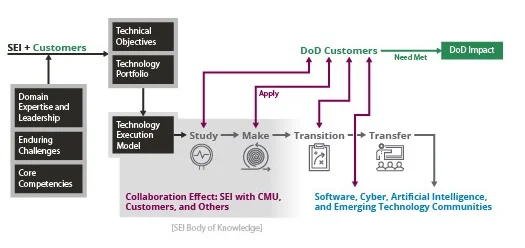
This SEI Blog post highlights how the SEI has reshaped its research strategy over the past several years to take on emerging disruptions, and how we’ve integrated a number of …
Read More•By Thomas A. Longstaff
In Software Engineering Research and Development

SEI Blog Archive
Recent
Year