Archive: 2022
Containerization at the Edge
Containerization is a technology that addresses many of the challenges of operating software systems at the edge.
Read More•By Kevin A. Pitstick, Jacob Ratzlaff
In Edge Computing


Creating a Proposal for Virtual Prototyping in 7 Steps
Engineers and scientists often do not know how to create a compelling proposal for a virtual prototyping program—especially the key software component—and obtain funding and support.
Read More•By Douglass Post (DoD High Performance Computing Modernization Program)
In Software Engineering Research and Development

Internet-of-Things (IoT) Security at the Edge
Assuring the security of any hardware device is a hard problem. In particular, Internet-of-Things (IoT) devices have increasingly been the target of malicious attacks.
Read More•By Sebastián Echeverría, Grace Lewis
In Edge Computing


Using Machine Learning to Increase the Fidelity of Non-Player Characters in Training Simulations
Use of machine-learning (ML) modeling and a suite of software tools to create decision-making preferences that make non-player characters (NPCs) more realistic in simulations.
Read More•By Dustin D. Updyke, Thomas G. Podnar, Geoffrey B. Dobson, John Yarger
In Cyber Workforce Development


A Case Study in Applying Digital Engineering
Case study of an SEI project in which digital engineering is being used successfully to provide visibility of products under development from inception in a requirement to delivery on a …
Read More•By Nataliya Shevchenko, Peter Capell


Improving Automated Retraining of Machine-Learning Models
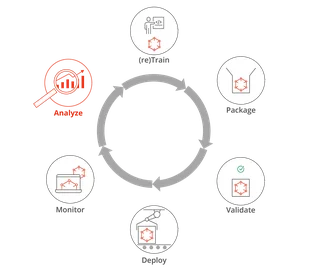
This post describes how to improve representative MLOps pipelines by automating exploratory data-analysis tasks.
Read More•By Rachel Brower-Sinning
In Artificial Intelligence Engineering

Six Dimensions of Trust in Autonomous Systems
This post chronicles the adoption and growth of autonomous systems and provides six considerations for establishing trust.
Read More•By Paul Nielsen
In Software Engineering Research and Development

Security Analytics: Tracking Proxy Bypass
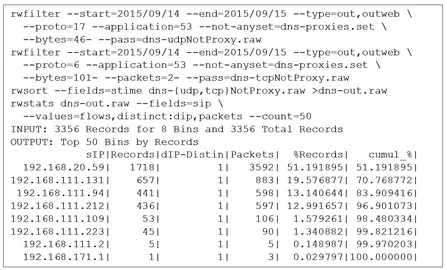
This post describes how to track the amount of network traffic that is evading security proxies for services that such proxies are expected to cover.
Read More•By Timothy J. Shimeall
In Cybersecurity Engineering

A Method for Assessing Cloud Adoption Risks
The move to a cloud environment provides significant benefits. Realizing these benefits, however, requires organizations to manage associated organizational and technical risks effectively.
Read More•By Christopher J. Alberts
In Cloud Computing

Cybersecurity Capacity Building with Human Capital in Sub-Saharan Africa
This post explores the creation of skilled cybersecurity human capital to solve real-life threats unique to the African continent.
Read More•By Angel Luis Hueca
In Cybersecurity Center Development

SEI Blog Archive
Recent
Year