KalKi: Solution for High Assurance Software-Defined IoT Security
Commercial Internet of things (IoT) devices are evolving rapidly, providing new and potentially useful capabilities. These devices can be a valuable source of data for improved decision making, so organizations that want to remain competitive have powerful motivations to embrace them. However, given the increasing number of IoT vulnerability reports, there is a pressing need for organizations to integrate IoT devices with high assurance, especially for systems with high security and safety requirements.
In this blog post, I describe KalKi, a software-defined IoT security platform that we are developing at the SEI. KalKi is designed to move security enforcement to the network, thereby enabling safe integration of commodity IoT devices, even if the devices are not fully trusted or configurable. KalKi leverages software-defined networking (SDN) concepts and constructs, combined with a policy model that specifies both cyber and kinetic attacks to create a safe, dynamic, and extensible platform for IoT device integration. As shown below, our experiments demonstrate high performance, scalability, and resilience, even in the presence of a powerful attacker.
The term KalKi is of Sanskrit origin, and is the name of an avatar of the god Vishnu, who is the destroyer of filth and malice (such as vulnerabilities and attacks) and usherer of purity, truth, and trust.
IoT Risks
The DoD currently uses IoT devices in supervisory control and data acquisition (SCADA) systems. It is also interested in using such devices in tactical systems. However, security concerns about, for example, vulnerabilities and untrusted supply chains, have discouraged widespread adoption of IoT.
- Not all device manufacturers follow secure development practices.
- Not all devices allow software updates, which leads to security software that is obsolete.
- The dynamic nature of the current device market results in inconsistent installation of security patches.
- There are few IoT security standards that are widely implemented by IoT devices.
IoT risks have been publicly identified in a number of incidents in recent years. In August 2019 Microsoft reported that hackers working for the Russian government were using printers, video decoders, and other IoT devices as a beachhead to penetrate targeted computer networks. In May 2019 a variant of the Mirai botnet was found using a total of 13 different exploits to target routers and other IoT devices. In November 2018 another botnet was discovered to have taken control of 100,000 home and small-office routers made from a range of manufacturers, mainly by exploiting a critical vulnerability that has remained unaddressed on infected devices more than five years after it came to light. In addition, CNET warned in August 2018 that your smart air conditioner could help bring down the power grid.
The causes of these incidents and others like them are rooted in the limitations of existing network-protection systems: gateways and firewalls can become compromised, and static firewalls are not device-specific and cannot adapt to changing security states.
The KalKi Solution
The SEI KalKi platform, based on SDN concepts and constructs, enables secure integration of off-the-shelf devices. Software-defined approaches to securing IoT deployments are a proven, viable approach for protecting the diversity of IoT devices and software stacks. KalKi moves part of security enforcement to the network to enable the integration of commodity IoT devices into DoD systems. Even if the IoT devices are not fully trusted or configurable, KalKi creates an IoT security platform that is provably resilient to a collection of prescribed threats.
KalKi adapts network defenses for each IoT device based on active monitoring of (1) traffic to and from each IoT device and (2) variables sensed by each device. This combination of network and device state enables the creation of security policies that combine cyber and kinetic attack conditions, thereby providing greater protections for the system.
Software-Defined Networking
KalKi uses SDN and network function virtualization (NFV) to create a highly dynamic IoT security platform. SDN is the concept of building a network architecture that decouples the packet-forwarding logic (i.e., control plane) from the packet-forwarding and processing hardware (i.e., data plane). The control plane resides centrally, whereas the data plane can be centralized or distributed based on network requirements and constraints.
NFV is a network-architecture concept in which functions traditionally performed by dedicated hardware, such as a firewall or an intrusion-detection system (IDS), can be implemented in software. In addition to improved manageability, NFV removes the cost and complexity of having different hardware appliances for different network functions. Once in operation, the NFV must be monitored for capacity and utilization, and adapted if necessary. All these functions can be accomplished by SDN, which is why NFV is one of the primary SDN use cases.
Tianlong Yu of the Carnegie Mellon School of Computer Science and colleagues proposed an architecture for enterprise networks that leverages SDN and NFV to provide
- context--customized policies for each device
- isolation--limited interference between security policies
- agility--rapidly changing security actions
In this architecture and others, each network device has its own set of NFVs (referred to as μmboxes and pronounced "micro-m-boxes") executing customized functions for that specific device (context and isolation). The current implementation of μmboxes is based on virtual machines (VMs). Moreover, the configuration of these μmboxes can be dynamically changed by an SDN controller (agility). KalKi builds on, implements, and extends the vision underlying these architectures.
KalKi Architecture and Implementation
The KalKI IoT security platform is composed of a control node, which triggers changes in the network defenses for each IoT device in the system, and a data node, which
- acts as a gateway between the IoT devices and the network
- monitors network traffic and sensor data to and from the devices
- deploys network defenses (i.e., security measures) for each device as instructed by the control node.
A dynamic view of the KalKi architecture is shown in Figure 1. The view shows the main components of the control and data nodes. The control node maintains the state of the devices as well as the policies that define how security measures change, and has components to evaluate these policies and to communicate with the data node. The control node can both receive alerts from the data node and send commands to deploy different μmboxes. The data node in turn has an Open vSwitch virtual switch that all traffic to and from the devices goes through, and that routes it to the μmboxes that are deployed at any time for each specific device, implemented as Qemu VMs.
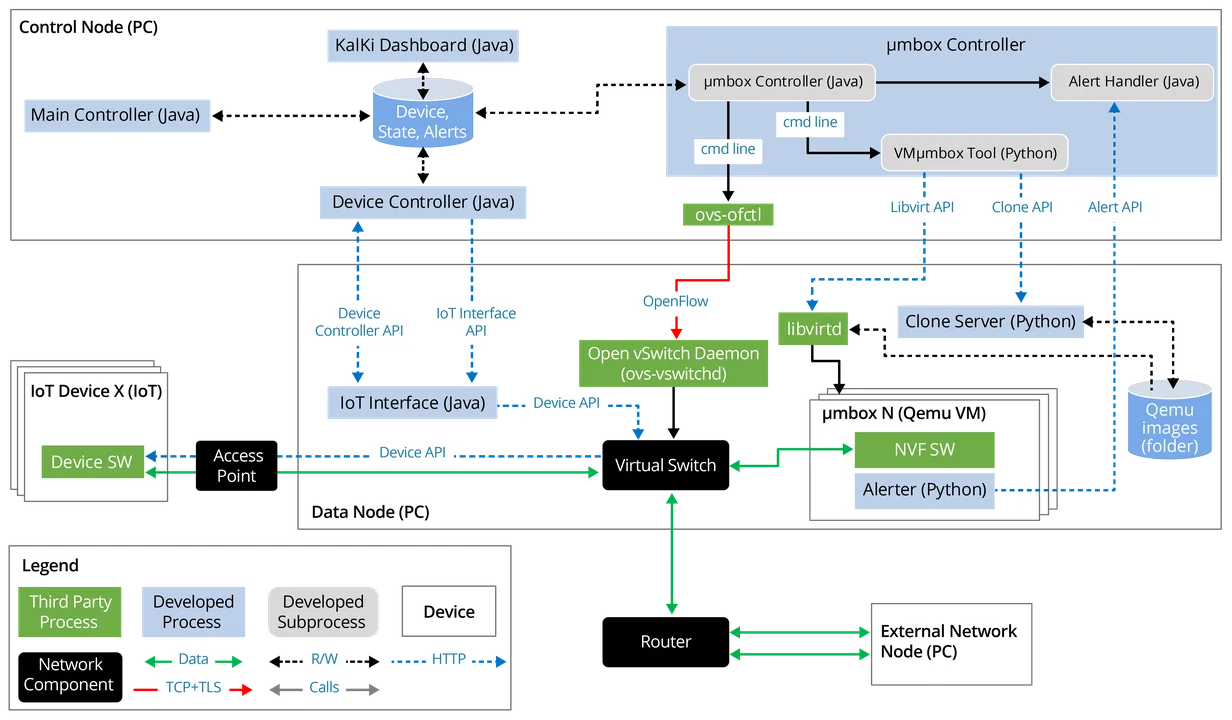
Figure 1: Dynamic View of the KalKi Architecture
Details on how the system monitors threats, changes security states and deploys security measures are shown in Figure 2.
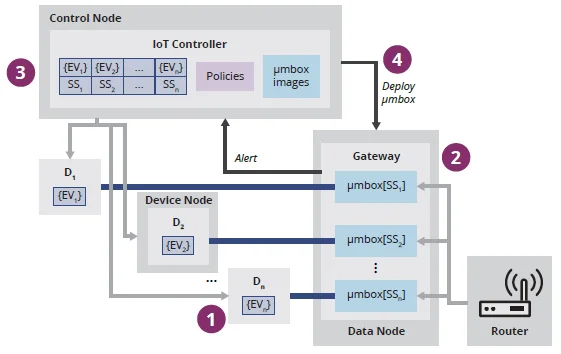
Figure 2: Data Flow for Security State Changes
Every step labeled in Figure 2 is shown below.
- Each loT Device D senses/controls a set of environment variables EV
- Network traffic to and from each device is tunneled through μmboxes that implement the desired network defense for the current system state.
D1 μmbox[SS1] = Firewall
D2 μmbox[SS2] = IPS, ...
3. An loT Controller maintains a state composed of {EV} and security state (SS) for each device
SS= {Normal, Suspicious, Attack}
4. Changes in the whole state for all devices are evaluated by policies and may result in the deployment of new μmbox(es)
Progress to Date and Next Steps
In the first year of this work, we defined an initial threat model to guide development, along with a policy model to set conditions to change security state and actions to take. We also produced an initial architecture and prototype of the IoT security platform and created an initial dashboard to configure the system.
In the second year, we fully developed the IoT security platform prototype. In the software-defined part of the prototype, we monitored device-specific vulnerabilities, supported different policies for each security state, and ran our prototype on commodity hardware/software.
We also updated the dashboard with creation of policies and μmboxes for four representative IoT devices. The dashboard enables real-time monitoring of security state and easy configuration of security policies. We conducted an experiment to test different scenarios and red-team attacks, executing multiple test scenarios to measure resilience to attacks, performance (time to react to threats), and scalability (effect of the number of devices in performance).
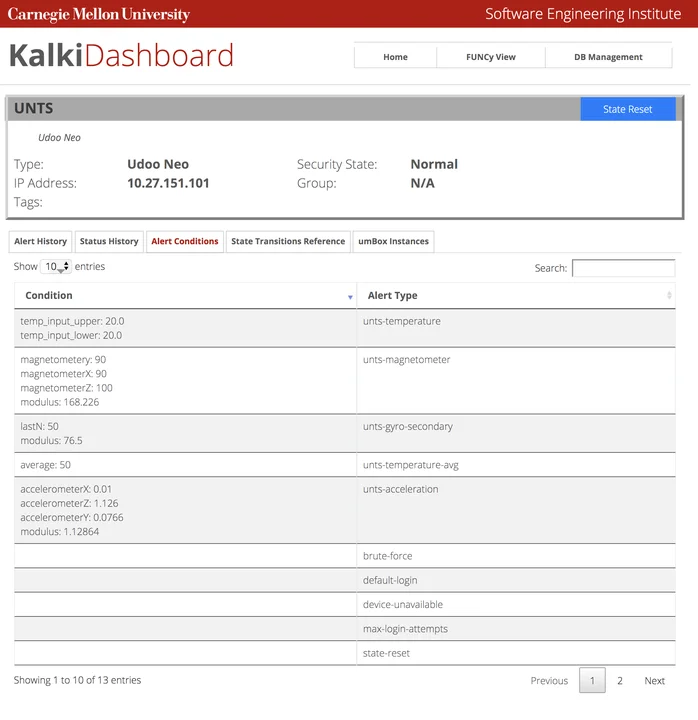
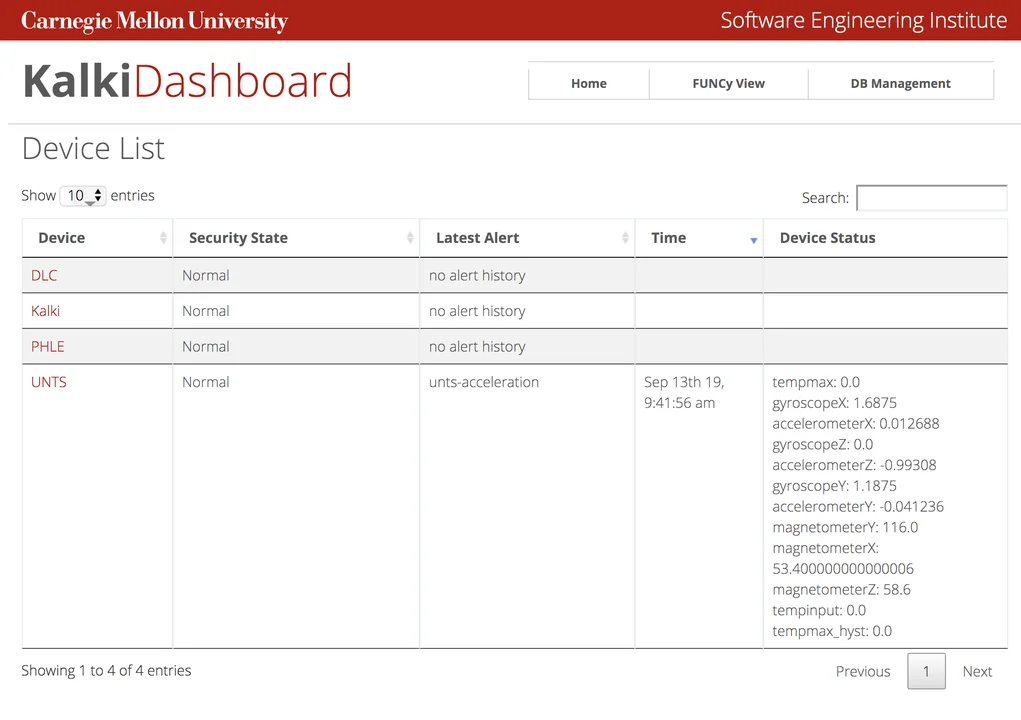
Figure 3: KalKi Dashboard with Real-Time Monitoring of Security State and Easy Configuration of Security Policies
Looking Ahead
KalKi enables the integration of commercial IoT devices into networks. It also protects those networks, even if IoT devices are not fully trusted or configurable. Initial experiments show that the platform performs well, scales well, and remains resilient in the presence of a powerful attacker. Benefits of using KalKi include monitoring of device-specific vulnerabilities, support for different policies based on security state, and flexibility to adapt to an evolving IoT market.
However, we also recognize KalKi limitations that are the focus of our current and future work:
- There are components of the system that if attacked would compromise the full system, including the main controller that contains the state machines used to control the network defenses for each IoT device. To address this problem, we are extending überSpark, implementing sensitive components as üobjects--low-level system constructs that are protected from other untrusted system components and that allow only authorized components to communicate with them.
- To improve performance of the system we are evaluating various strategies, such as starting all VMs upon platform bootup and moving to Docker containers.
- We plan to investigate artificial-intelligence and machine-learning techniques that can more intelligently detect new attacks or exploits, or reduce IoT device integration time by automatically generating security measures or policy definitions based on learning of normal and abnormal IoT-device behavior.
Our next steps in the upcoming third year are to complete and optimize development of our security platform, simplifying integration of new devices and policies, increasing performance, and reducing resource utilization. We are also seeking collaborators to pilot and extend this work. If interested, please contact us.
Additional Resources
Watch a video presentation about KalKi by SEI principal investigator Sebastian Echeverria.
Download presentation materials about KalKi.
Download a poster about KalKi.
Read more about überSpark in this paper from Usenix 2016.
More By The Author
More In Edge Computing
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Edge Computing
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
